Back in the days of Windows XP IT administrators could disable the local administrator account on domain joined computers but still be able to use the account if they rebooted the computer into safe mode (see How to access the computer after you disable the administrator account ).
To log on to Windows by using the disabled local Administrator account, start Windows in Safe mode.
However this behaviour has change since Windows Vista (and 7) and now you are no longer able to logon to a computers local administrator account if it is disabled (see Built-in Administrator Account Disabled ).
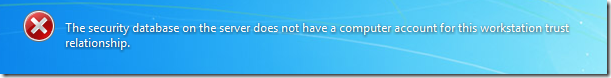
On domain joined computers, the disabled built-in administrator account cannot logon in safe mode
This presents some challenges as IT administrator as sometime you still need to ability to logon to a computer using the local administrator. The most common scenario you need to do this is when you need to troubleshoot domain account issues (e.g. re-join the computer to the domain) when the AD computer account has been reset or deleted or the password has become out of sync and you get a workstation trust relationship issue (see below).
The problem is that the local administrator account is now disabled and due to the new behaviour of the account you can no longer log with it using safe mode.
The built-in administrator account is disabled by default in Windows Vista on new installations.
This of course makes it almost impossible to configure the computer into a workgroup so that it can then be re-added to the domain to fix the problem. Its even more difficult if you have BitLocker encryption enabled on your local hard drive.
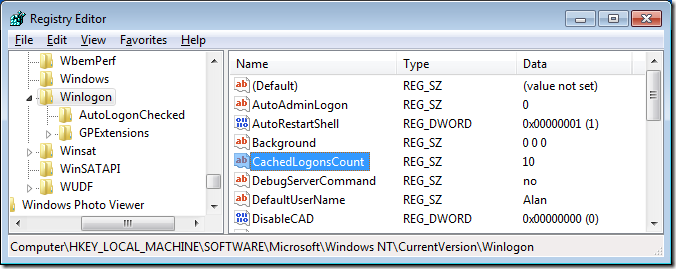
It is possible that you could logon with a user with local administrator access using cached credentials however this is limited to the last 10 people that logged on (increasable to 50 if you change the CachedLogonsCount below registry key).
But even so, this would also mean you have to know the username and password of the account at the time they last logged onto the computer. This may be a bit hard to do as they may have changed their password a number of times since they logged on to that computer.
Unfortunately, it is also much more unlikely now that the normal local user of the computer has not been given local admin due to all the improvement with Windows 7 (e.g. UAC) that allows users to work with standard user permissions.
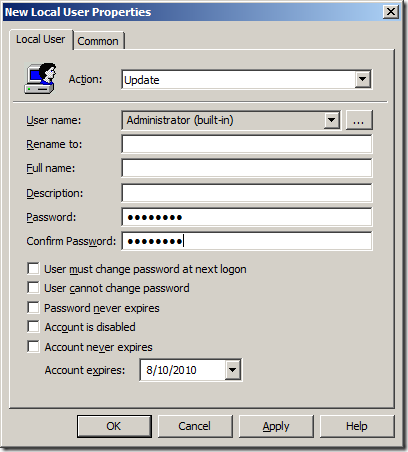
Now you might think the really obvious solution is to just enable the local administrator account and set a password in advanced using Group Policy Preferences (see below) so that you can use it when you need to however doing this has a few security issues.
However enabling the local administrator account means it can be used by anyone who knows the credentials and they could then use the account to remotely access any workstation on the network (not good). It also mean a normal user that knows the local admin credentials ( we would like to think they don’t but somehow they find out) could us them whenever they are presented with a specify credentials UAC prompt. So it’s pretty much a back door that anyone can use to get around the fact you spent all this time setting up their computers for them to not require local administrator access…
So to get around this issues you could just set the password on a regular basis using Group Policy Preference (see above image) however this also has a few problems as well… While setting the local administrator password is easy to do however it is stored in the SYSVOL as an encrypted string that is fairly easy to crack (see Passwords in Group Policy Preferences ).
To help mitigate this I have also written an article that explain a way to more securely apply the new password to all the computers (see How to use Group Policy Preferences to change account Passwords ) but even if you did this on a regular basis you would still need to tell all the IT support staff what the new password is when you change the password and thus people quickly learn the local admin account credentials all over again…
Note: That all being said it is still a really good idea to set a password for the local administrator account as the default password is configured as blank.
The other solution you might think of is to boot the computer using a third-party tool that can reset and enable the local admin account (see http://www.bing.com/search?q=sethc.exe+%22windows+7%22+administrator+password&form=QBRE&qs=n&sk= ) however these tools don’t work if your local drive is encrypted with BitLocker nor are they supported from Microsoft (see Microsoft policy about lost or forgotten passwords ).
So lets assume you have a computer that is no longer properly connected to the domain with a disabled local administrator account. The computers local system drive is BitLocker encrypted and and you don’t know the credentials of any other accounts that have previously logged on with local administrator permissions… What do you do?
So below I will show you how to enable the local administrator account so that you can at least still logon with the local administrator even if the account has been disabled…




Blog Post: How to enable a disabled Local Administrator account offline in Windows 7 (even when using BitLocker) http://bit.ly/c787fh
How to enable a disabled Local Administrator account offline in Windows 7 (even when using BitLocker) http://j.mp/dbyDue
RT @xenappblog: How to enable a disabled Local Administrator account offline in Windows 7 (even when using BitLocker) http://j.mp/dbyDue
How to enable a disabled Local Administrator account offline in Windows 7 (even when using BitLocker) http://t.co/ABtnFes
G’day Alan,
This is a good post and goes nicely alongside the post I recently made on how to reset an Administrator password in Windows Server 2008 R2/Win 7 (and WS2K8/Vista) in case you’ve forgotten it (like I did) or someone changed it and doesn’t remember it (or it can’t be beaten out of them).
The link to my blog post is: http://hiltont.blogspot.com/2010/09/reset-password-in-windows-server-2008.html – I hope this also helps someone out…
wow this saved my a$$ great article!
Thank you very mach
its wonderful
This the only site which helps me and solved my crisis…
Thanks so much indeed
Really a great article,it worked.
thanks a bunddle.
Handy article, worked fine – except that when I then log on as local administrator, it won’t let me do a lot, e.g. (most relevant here, obviously) control panel -> system -> advanced system settings: it does nothing. Really nothing – no “access denied”, no error messages of any sort, no events logged. Just nothing.
Any suggestions? TBH if I can’t fix it quite quickly it’ll be easier to reinstall the whole thing
After you have enabled the account are you rebooting and going back into normal mode?
Or is your administrator account actually an admin? or just a dummy admin account.
You just saved my ass. I didn’t realize my localadmin account was disabled when I disjoined my bitlocker encrypted laptop from the domain. Kind of embarrassing… think I’ll just sweep this one under the rug 😉
Very Helpfull article
Boom Click! You sir, are a genius. I didn’t have Bitlocker, but Windows 7 did have a disabled admin account. I used Trinity Boot Disk to blank the admin password and your registry change to unlock my disabled admin account. Yay!
Neat article, but I found a quicker way, turn off the computer, unplug the NIC, turn it back on, log on as the domain admin . Once logged back in, plug the wire back in, unjoin the doamin, reboot (first set Local admin password if needed), rejoin domain.
Great info, but how did you know that a value of 10 would make it work rather than any other? I guess what I’m getting at is: do you have a reference guide that lists different values and their function. For example: expiring an account, unlocking an account, etc?
Worked perfectly and I shared it with the rest of my staff. 🙂
I got right to the end but where I had to change 11 for 38, the 11 wasn’t there. infact it wasn’t anywhere in the binary string???
any ideas. I really don’t want to reinstall this laptop
thanks
I operate on win 7 ultimate. My ONLY login account was an administer account. The account has become disabled and I am told to see my administrator on each attempted logon. I have tried to boot up using the win 7 ult installation disk. It will not boot from the disk. I have tried to enter safe mode but it will not boot in safe mode. Any suggestions on how to bypass the disabled Windows logon?
Great article
this described exactly the problem I had, and this is the only article I found on how to solve the problem!
After enabling the BitLocker on the system drive, the registry files should be inaccessible. Every time when I get locked out of my computer, I’ll use PCUnlocker Live CD and it can reset password and unlock/enable user account.
Perfect walkthrough. Just saved my bacon. Your instructions couldn’t have been any clearer.. thanks!
When I purchased this emachines computer, it had Desktop Gadgets on it. I noticed after several months of use that the clock and temperature were blank. Updating Windows seemed to help a few times but eventually I got a notice that Desk Top Gadgets were corrupted. It’s still on the list when I click on the start button so I clicked on it. A block came up stating “Desktop gadgets are managed by your system Administrator”. I thought I was the administrator since this computer is for home use only. How do I access Group Policy to list myself as administrator so I can access Desktop gadgets?
Amazing! You saved me a day of work. Thanks!
Hello There. I found your weblog using msn. That is a really neatly written article.
I will make sure to bookmark it and come back to read more of your helpful information.
Thank you for the post. I will definitely comeback.
Hi Alan,
that’s a very great article. i have same issue with the encryption using Win 7. but the encryption software was not bitlocker. i am using mcafee safeboot.
do you any clue to enable local admin encrypted with safeboot ?
waiting for your update.thanks
What’s the deal, the article ends without explaining anything and all the fake comments on here just link to the same article.
“So below I will show you how to enable the local administrator account so that you can at least still logon with the local administrator even if the account has been disabled…”
and then nothing?
Hi
You must see Pag 2.
Oh. My. I upgraded an old computer in the office to windows 10 that used to be connected to an old domain. The new install disabled the local admin account and we were locked out. You can’t log in to safe mode without domain credentials… Nothing. Changing that value worked! I also disconnected the network cable at the same time, but I’m attributing it the regedit. I also initially made the mistake of trying to open the wrong Sam file at first. Make sure you browse to the d: drive!! Thank you!!
Awesome…..it worked! thank you very much!
It’s in fact very complex in this busy life to listen news on TV, so
I simply use internet for that reason, and get the latest news.
Nice Work & a Great Knowledge About Windows 7 Thanks For Sharing Such Kind of Helping Material From: http://www.jojosoftwares.com/uncategorized/emsisoft-anti-malware-license-key-full/
Thank you.
This worked great! Luckily, we have 2 admin accounts on ours because one was Locked as well as being Disabled. Is there a way to Unlock these accounts as well?
To activate a locked or disabled Windows account, use a boot media to boot off your PC:
http://www.top-password.com/knowledge/enable-built-in-administrator-account-to-log-on-windows.html
Worked on Windows Server 2016 too
…thank you….
I can finally sleep because I found your baller guide. None of our company’s enterprise programs could boot from uefi, so they couldn’t see the new nvme drives’ SAM file. Tried so. Many. Things.
This was the one that worked. Also this taught me exactly what those tools do! I have become the tool!
Wait…that’s not right