A long time ago did a blog post explaining how to use the Group Policy Preferences Local Users setting to manager the password of the local accounts. This post explained how to do it in a way that minimised the exposure of the password in Active Directory (see How to use Group Policy Preferences to change account Passwords ) for anyone that knew what they were doing.
At least as far back as 2009 (and certainly earlier) it was well known that the password was only weakly encrypted and as such could be easily reverse engineer to recover the password. However, for a long time this was much better than the alternative as a lot of administrators would often revert to using scripts that had the password stored as clear text.
Update: Microsoft has now released MS14-025 which explicitly blocks the configuration of passwords in Group Policy Preferences. See more about this at Group Policy Preferences Password Behaviour Change – MS14-025
Microsoft has also gone to extensive lengths over the years to warn users about risks of using password in Group Policy preferences:
1. Via blog posts at Passwords in Group Policy Preferences (updated)
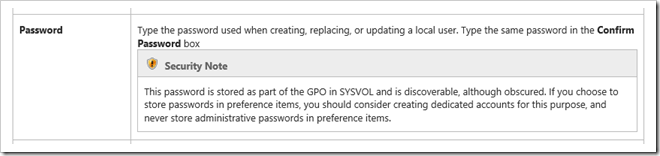
A password in a preference item is stored in SYSVOL in the GPO containing that preference item. To obscure the password from casual users, it is not stored as clear text in the XML source code of the preference item. However, the password is not secured. Because the password is stored in SYSVOL, all authenticated users have read access to it. Additionally, it can be read by the client in transit if the user has the necessary permissions.
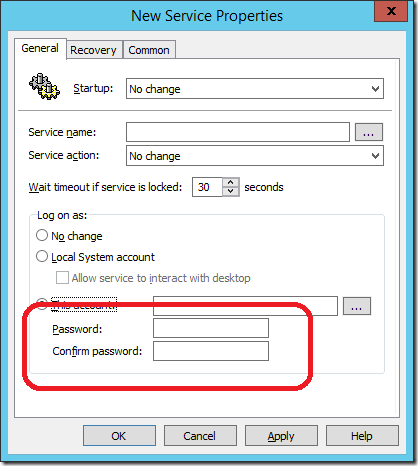
2. When you look up the Local Users Group Policy Preferences warning it says this…
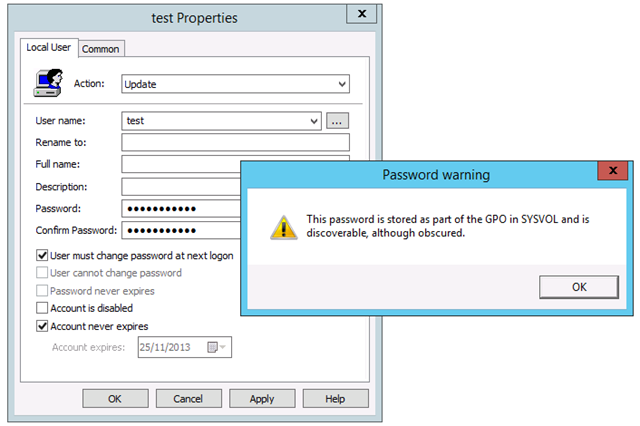
3. And when you actually configure the password you are warned again before setting the password.
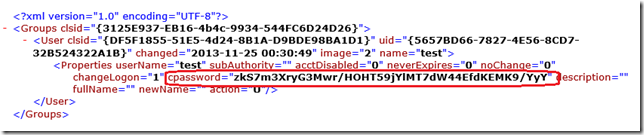
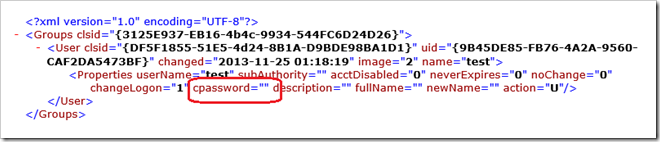
So how weakly encrypted is the cpassword?
The CPASSWORD is the filed that is used in the Group Policy Preferences XML configuration file that contains the password. Being an XML file this makes it very easy if find the field by simply looking a the contents of the XML files stored in you SYSVOL.
AND….
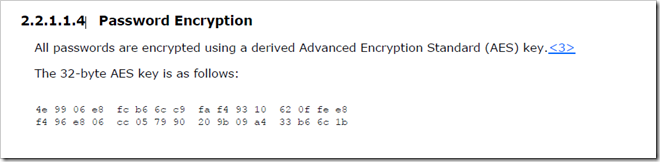
Microsoft documents the password that us used to encrypt/decrypt using AES 32-byte encryption (VERY WEAK). If you would like to see the password for yourself it can be found in the official technical specification at http://msdn.microsoft.com/en-us/library/cc232587.aspx or… in the modified screenshot provided below (yes that is the ACTUAL key used to encrypt password in Group Policy).
Now you might be thinking that it is absurd that Microsoft are publishing the key used to encrypt the password however due to the DOJ settlement with Microsoft back in 2001 Microsoft are required to document its application programming interfaces with third-party companies. This means that the Microsoft are compelled to document this information…
And now for the REALLY BAD NEWS….
Since June 11th 2012 there has been a Group Policy Preferences Password module added to MetaSploit that allows you to scan you to discover all the uses of passwords saved in your Active Directory (see description below).
This module enumerates the victim machine’s domain controller and connects to it via SMB. It then looks for Group Policy Preference XML files containing local user accounts and passwords and decrypts them using Microsofts public AES key. Tested on WinXP SP3 Client and Win2k8 R2 DC.
Reference: https://www.rapid7.com/db/modules/post/windows/gather/credentials/gpp
So what does this really mean?
Any users that has the MetaSpoit tool installed on their computer and has an account on your domain can scan your Active Directory and decrypt the stored value of password in a Group Policy Preference . Of course once they have the password of the account they can probably use that account which quite often has elevated privileges…
What Group Policy Preferences are affected ?
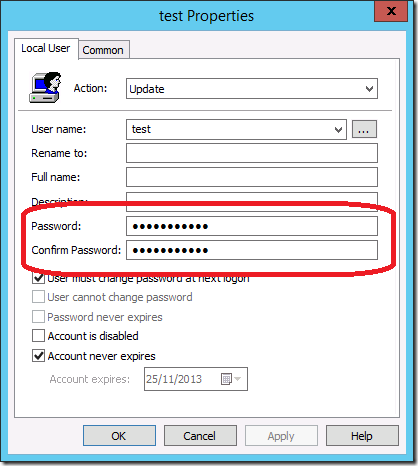
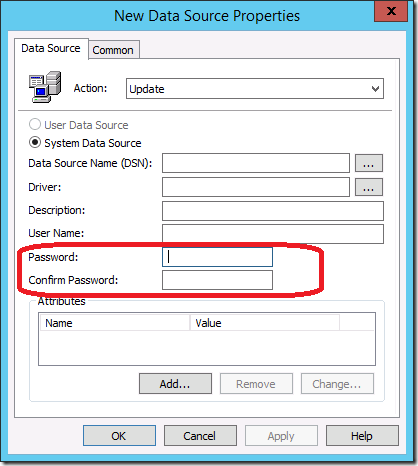
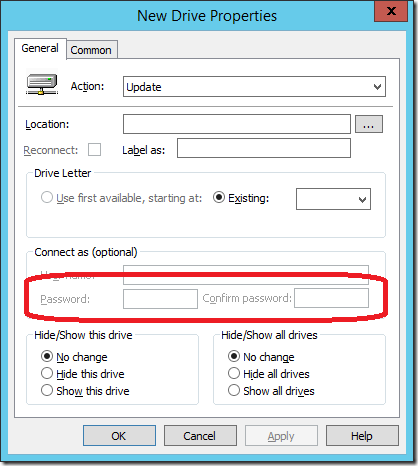
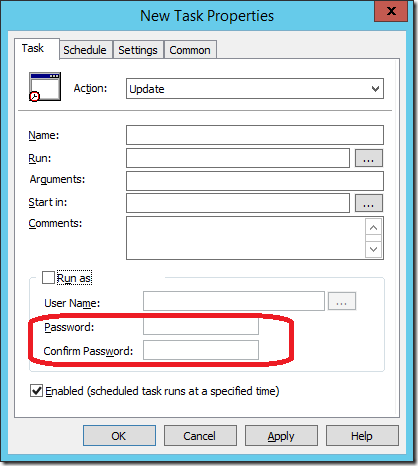
While in this post I have focused on the Local Users account password option this is not the only location that you can save a password. In fact there are five separate location in Group Policy Preferences that a save password option can be found.
- Local User preference items
- Data Source preference items
- Mapped Drive preference items
- Scheduled Task or Immediate Task preference items
- Service preference items
Update: How do I know here I have this password configured?
Darren Mar-Elia at SDMSoftware has now written a PowerShell script that allows you to identify all the location in your domain that the Group Policy Preference password exists. Check it out at http://sdmsoftware.com/group-policy-blog/tips-tricks/getting-rid-of-passwords-in-group-policy-preferences/
Should I blame Microsoft for this security issue?
In my opinion, No. This security risk as been in Group Policy Preferences ever since Microsoft bought PolicyMaker. They have also documented a number of time (see above) the risks associated with using this option. Security is also an ever changing field and at the time even weakly encrypted password was better than what most IT administrators otherwise did to do the same task.
So what do I do?
Firstly… Stop configuring any new password in Group Policy Preferences.
Then to find any XML files stored in your SYSVOL (yes there will be a LOT). Open the XML files and then find any that have a configured CPASSWORD value and remove them using either using the Group Policy Preferences UI or by just delete the value our of the XML manually. Once this is done the password value is set to null thus removing the value from Active Directory and mitigating the risk.
As they are Group Policy Preferences the value will persist on the computers/accounts that are already configured. However any new computers will not get the new value configured so keep this in mind as it will probably affect any computer build process you already have in place that uses this setting.
And yes… this means you will need to implement an alternative way to manage password on your computers in your organisation.
Certainly all this news a PITA, however it is something as a Group Policy administrator you must be aware of and actively stop in your organisation…
Additional References: Group Policy Preferences Password Behaviour Change – MS14-025NICE





Hi Alan, what timing. I am just updating the local admin password in our company. I have read all your articles (excellently written and explained) regarding using GPP and the local admin password. We made the decision to deploy and run Jeff McJunkin’s Randomizing the Local Administrator Account Password vbs script. Using preferences we are pushing the script down to the client machines (once) and running the script from the RunOnce registry key (Once) and for good measure, disabling the local admin and guest accounts. Keep up the good work. @GeniMatt
I have also seen script solution that generate a random password for the local admin account and then saves it to a file share that only allow computers to write (not read) the password for the computer.
Hello Alan,
i deploy the password for the local admin account with GPP. I use security filtering, so that the gpo is only applied to domain computers. If you try to navigate to the corresponding group policy folder (sysvol) with a standard domain user account, access is blocked. So, is this secure enough?
Thank you,
No, someone could use the context of the computer account to get access to this file. It is also unusual that you cannot navigate to the SYSVOL folder as a normal user. It’s BAD…. ALWAYS BAD
Hi Alan,
no, not the whole sysvol folder is blocked, just the corresponding folder of the gpo – so that only computer accounts can read the xml file where the password is saved (%sysvol%\domainname\policies\{GUID}…
But how is it possible for a standard domain user (with or without local admin privileges) to use the context of the computer account to get access to that file? Can you make an example on how to achieve that?
Thank you,
Use something like psexec to launch a command prompt.
psexec -s, will run as the local system. If you’re a local admin then you can impersonate the local machine.
Hakan Onder liked this on Facebook.
Csaba Hegedüs liked this on Facebook.
Anthony Buonpane liked this on Facebook.
Pam McLeod liked this on Facebook.
Robert Wrobel liked this on Facebook.
Eric Lane liked this on Facebook.
Sony Nair liked this on Facebook.
Farhad Entessari liked this on Facebook.
Ashraf Hussain liked this on Facebook.
Santiago Buitrago liked this on Facebook.
Why Passwords in Group Policy Preference are VERY BAD http://t.co/sa3nwE7bNS
The Scripting Guy had a recent post on storing credentials securely (http://blogs.technet.com/b/heyscriptingguy/archive/2014/03/25/use-powershell-to-explore-office-365-installation.aspx) for use in connecting to Office 365. He referenced a link about the Microsoft Data Protection API (http://msdn.microsoft.com/en-us/library/ms995355.aspx#windataprotection-dpapi_topic04) and I wonder if this technology with PowerShell could be leveraged to change passwords securely? Your thoughts would be greatly appreciated.
Oops! That page can’t be found.
Axel Rornk liked this on Facebook.
Hello Allan, i’ve recently configured LAPS in our environment. I had GPO configured to update password to local account to all machines in the network. My problem here is the password that LAPS generated on attribute is not working. Not sure if you hane any idea with this. Please help.