Tutorials
How to use Group Policy Preferences to manage Windows Power Plans
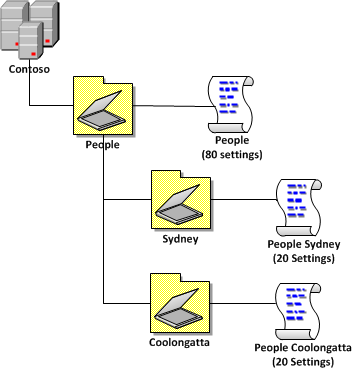
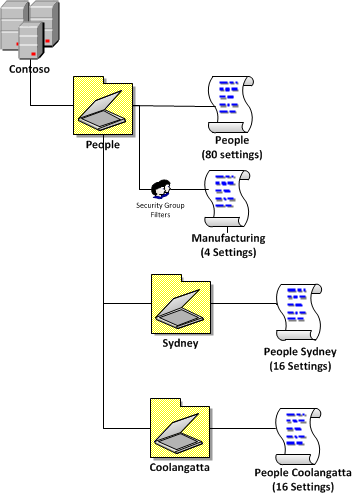
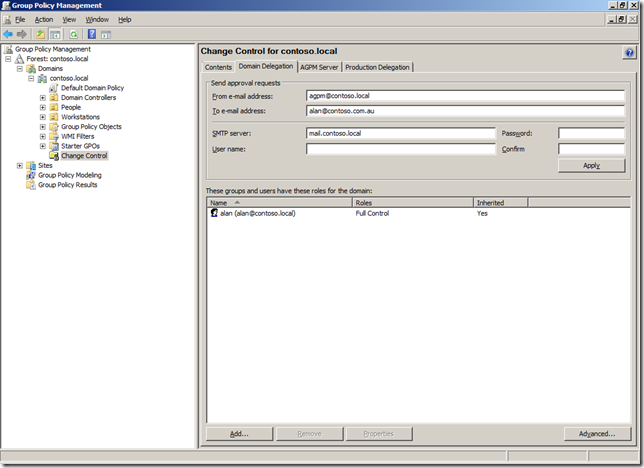
One of the new feature of Group Policy Preferences in Windows 7 and Windows Server 2008 R2 is support for configuring power plans using preferences for Windows Vista and later (see Image 1). You used to be able to control power management in Vista using native policies however the advanced targeting of preferences now enables lot of new scenarios with power savings. AWSOME!
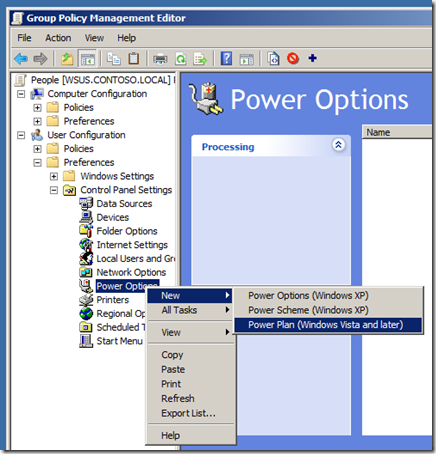
Image 1. Creating a new Windows Vista and Later Power Plan
One of the really neat things that you can do with Group Policy Preferences (GPPâs) and Targeting is change the power scheme of a computer based on the time of the day and the day of the week. This allows you to apply more aggressive power plans to your workstations after hours but then then back off during the day when people are working. Even though that Windows Vista (and Windows 7) support adaptive display time out which backs off the screen saver timeout when a user is still sitting at a computer but not actively using it they still have to wake up the computer by before the timeout started to back off. Applying the less aggressive power plan during working hours means that the user is less likely to have to keep waking up their computer in the first place as you have configured longer time out values.
Now if this sounds familiar youâd be right as I did demo some of this during my TechEd Australia Group Policies session that I did with Lilia Gutnik and it is similar to the TechNet Edge video by Michael Kleef and Mark Gray. But in this article I am going to diving a lot deeper than my demo or in the TechNet Edge video.
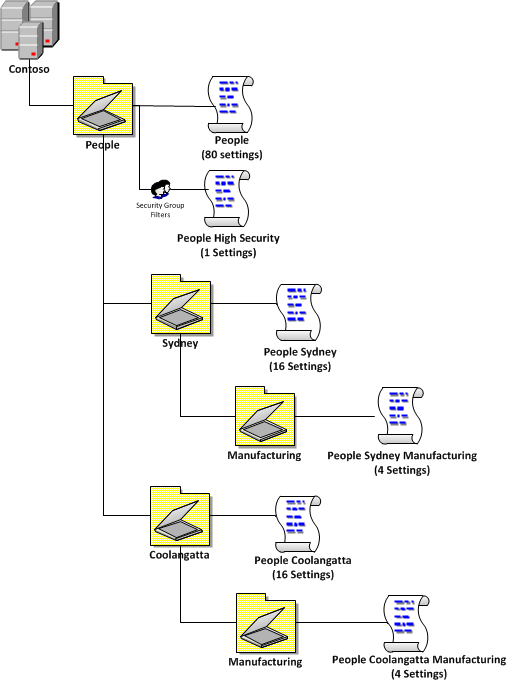
So before we talk about how to do this first lets go over what we are trying to achieve. We are assuming you manage a fleet of workstations that are only used during standard business hours and afterhours you want the computers to go to use as little as power as possible. You want to apply different power plans to the computers not only based on the day of the week but also the time of the day to make sure you get maximum possible power savings (see Image 2).
Image 2. Example power plan timetable
So to do this we setup two separate power plans, with one that is applied by default all the time and the other one that will take precedence and apply during business hours.
How to setup the Default Power Plan Policy
Step 1. Create a Power Plan under the User Configuration option of a GPO that has has aggressive power savings configured without any targeting other than being applied to all the users you want to control the power plans. I will leave the exact details of the power plan up to you but I will recommend that if you are going to set the âSleepâ timeout for Windows Vista (or greater) then make sure you also enable the âAllow hybrid sleepâ option (even on your desktops) (see Image 3.) as this will protect your computers from data loss if you lose power to your office environment afterhours.
Image 3. Enable hybrid sleep mode
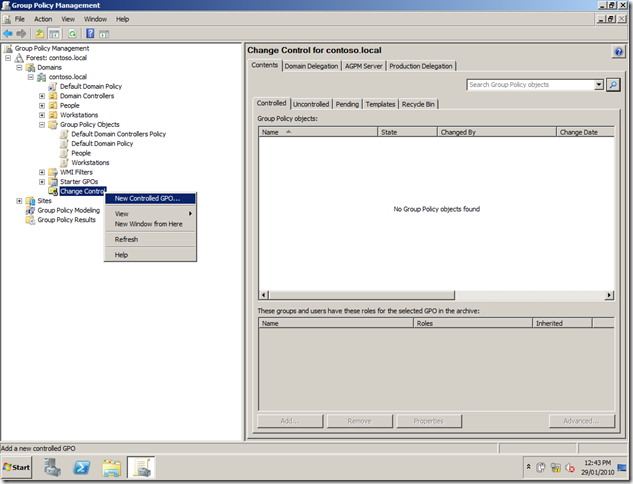
Step 2. Rename the item to be called something like âDefault Power Planâ (see Image 4) and also make sure that it is always set to order number one.
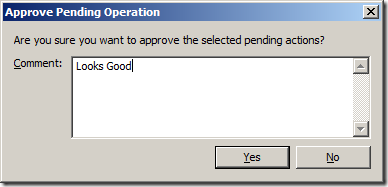
WARNING â If you do this make sure you either immediately disable the item (tool bar > red circle âdisable this itemâ) or setup the Business Hours Power Plan straight away so that you don't start shutting down all your computer during the middle of the day.
Image 4. Default Power Plan at Order 1
How to setup the Business Hours Power Plan Policy
Step 3. Create another Power Plan setting item called âBusiness Hours Power Planâ (see Image 5.) making sure it is lower order than the default power plan. Again I will leave the exact settings up to you but this one should be less aggressive than your default power plan.
Image 5. Business Hours Power Plan
Step 4. Now go into the properties of the âBusiness Hours Power Planâ
Step 5. Click on the Common Tab and tick âItem-Level Targetingâ
Step 6. Click on the targeting button
First of all we are going to create a collection that will target the Business House Power Plan to only the weekdays of the week.
Step 7. In the targeting Editor click on âAdd Collectionâ (see Image 6.)
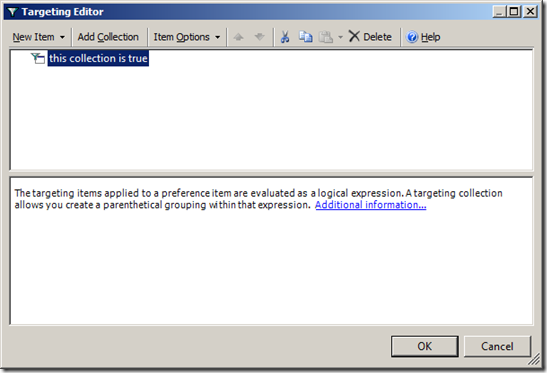
Image 6. Creating a targeting collection
Step 8. Click on the âNew Itemâ and then click on âDate Matchâ (see Image 7 & 8.)
Image 7. Creating a Date Match rule
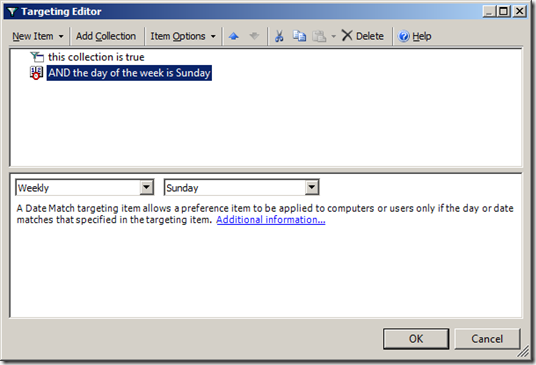
Image 8. Date match rule before being dragged into a Collection
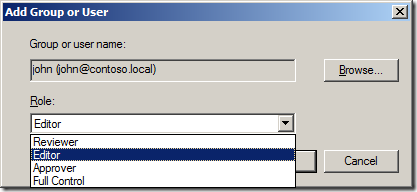
Step 9. Now you will need to drag the âAND the day of the week is Sundayâ onto the âthe collection is trueâ and change the day to âMondayâ (see Image 9.)
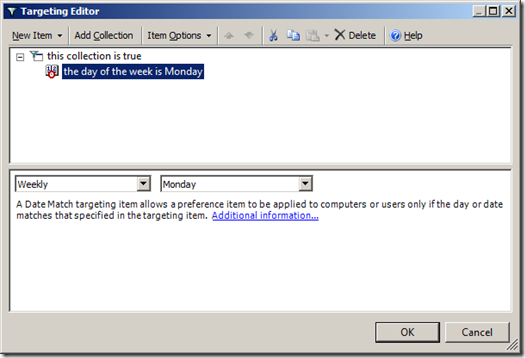
Image 9. Date Match rule after being dragged in the collection.
Step 10. Now make sure that âthe day of the week is Mondayâ is highlighted and click CTRL-C once and CTRL-V four times to copy and paste the date match rule once for each weekday (see Image 10).
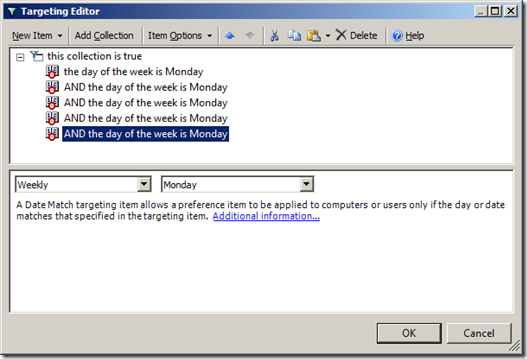
Image 10. Five date match rules in one collection
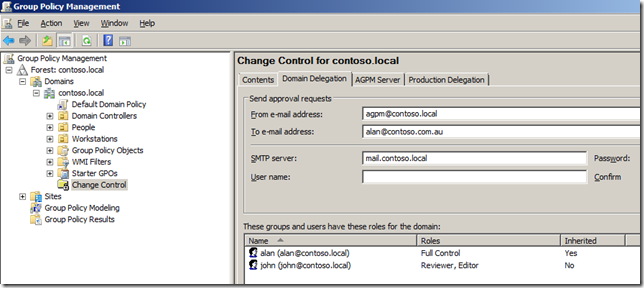
Step 11. Now click on each of the âAND the day of the week is Mondayâ and press F6 to change each date match rule from and âANDâ to a âORâ and then change the days to Tuesday , Wednesday, Thursday and Friday (see Image 11).
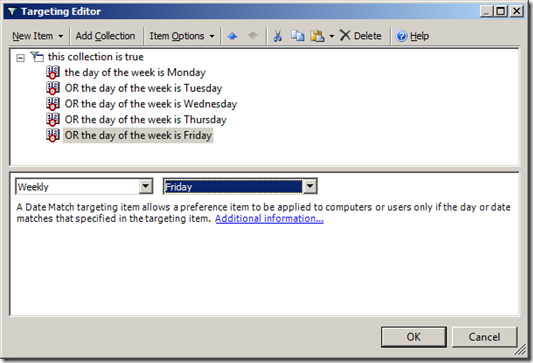
Image 11. Data Range Collection configured to apply only during weekdays
Now we will add a Time Range option that will refine when we target the Business House Power Plan to just working hours of the weekdays.
Step 12. Click on the âthis collection is trueâ and then click on âNew Itemâ and then click on âTime Rangeâ (see Image 12).
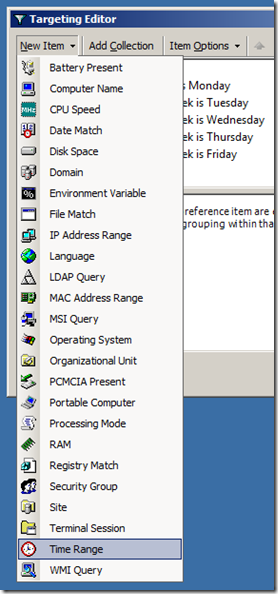
Image 12. Adding Time Range to targeting
Step 13. Now configured the time range to when during the day you want to Business Hours Power Plan to apply (see Image 13).
Note - Make sure you allow for the policy refresh interval (default 90 minutes with a 20% random offset) when configuring the start and end time. This means you might want to start applying the policy 2 hours before the start of business (e.g. 6:30am) to make sure all the computers are configured with the Business Hours Power Plan before people login in the morning (e.g. 8:30am).
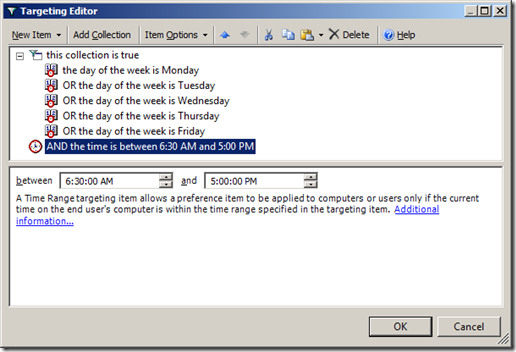
Image 13. Targeting configured with Date Range collection and a Time Range
Now you have configured a Group Policy Preference to apply less aggressive power plans to your computer during business hours while still having more aggressive power plans applied after hours.
Other Option - More user Control
In the example above we just modified the âBalancedâ power plan setting when we wanted to make changes to the power settings. If you did not want to give your users some more control and not force specific power plans you could just select the âHigh performanceâ plan and tick âSet as the active power planâ for the Business Hours Power Plan (see Image 14) and the âPower Saverâ plan as active in the Default Power plan (see Image 15).
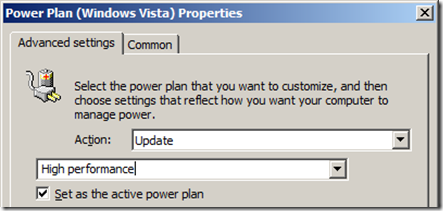
Image 14. Setting the High Performance plan as active
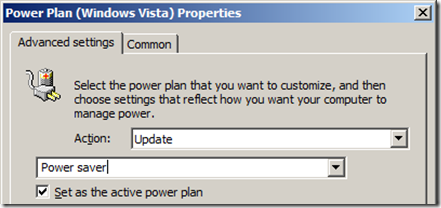
Image 15. Setting the Power Saver plan as active
This way your users can still configure each of the power plans to their own preference but you will still make sure that the âPower Saverâ plan will be applied to your computers after hours. However as you are only setting which plan is active then your users could get around the power plan as by configure both plans to never time out thus negating the benefit of any of the planâs.
Other Options â Less aggressive Default Power Plan
You may also want to set the default power policy to be less aggressive by default and then apply the aggressive power as the second item in the list using a little more complicated targeting (see Image 16). The advantage of this method is you can easily turn off the aggressive power savings plan when you want to do afterhours by just disabling the âAfterhours Power Planâ.
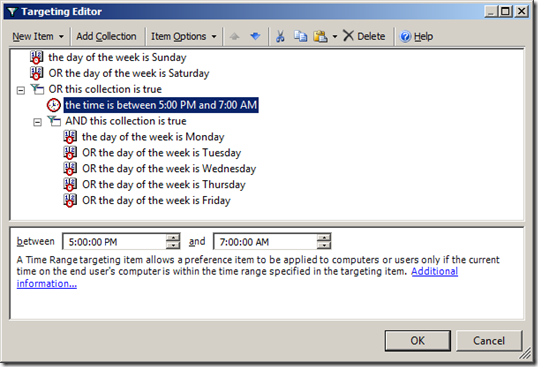
Image 16. Targeting to apply plan only afterhours
How to delegate AD permission to Organisational Units using the PowerShell command Add-QADPermission
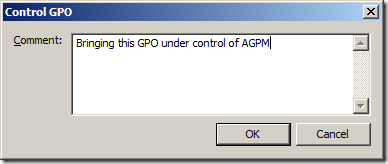
Recently, I have been working a lot with PowerShell to automate the creation of a full AD site OU structure (with Group Policy and all) along with all the necessary delegated permissions. One of the limitation of the out of the box AD PowerShell commands is there is no easy way (but apparently there is a really hard way) to delegate permission to Active Directory OUâs. Luckily Quest Software have helped a lot here and they have offered a set of FREE PowerShell commands for Active Directory called âActiveRoles Management Shell for Active Directoryâ one of which is called Add-QADPermission which greatly simplifies the process of delegation security in AD.
The Add-QADPermission command can be used to add an DACL security descriptor permission to any AD object with a distinguished name such as users, computer or OUâs. Therefore you can use this to delegate permission to OU similarly to running a âDelegation of Control Wizardâ in Active Directory Users and Computers console (see image below).
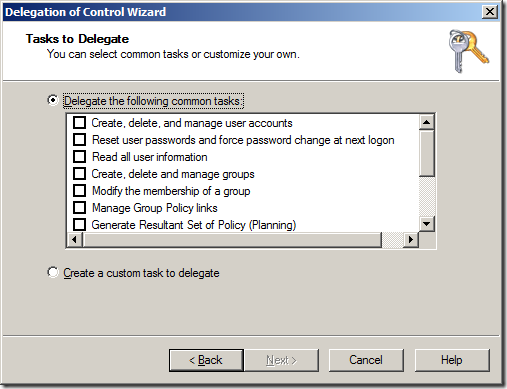
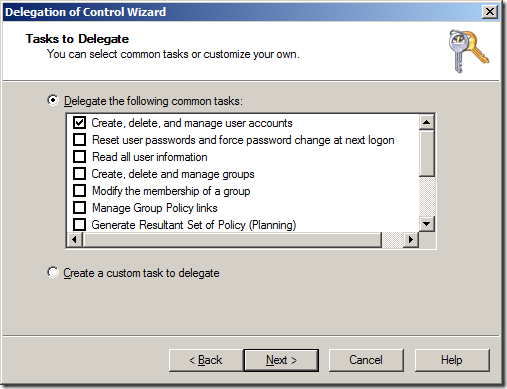
This wizard allows you to delegate some common tasks (see below) to your OUâs in you Active Directory however the permissions they apply are not straight forward simple permissions.
 |
 |
What I will show you how to do is how to perform some of the common delegation tasks that the âDelegation of Control Wizardâ using a PowerShell command so you can automate the process for creating new OUâs in your environment. I know this is not strictly an Group Policy topic but it is one closely related and one I think many Group Policy admins will find useful.
The Command tasks I will show you are the oneâs that I almost exclusively use when delegating permissions to Active Directory, they are:
- Create, delete and manage user accounts
- and Groups
- and Computers
- Reset user passwords and force password change at next logon
- Modify the membership of a group
Getting started â Installing the ActiveRoles Management Shell for Active Directory
The Add-QADPermission command is a third party PowerShell command so you will need to first download and install the new commands from the Quest site on the computer that you will be running the PowerShell commands. You can download the Quest ActiveRoles Management Shell for Active Directory from here http://www.quest.com/PowerShell/activeroles-server.aspx and then install the MSI file.
Installing ActiveRoles Management Shell for Active Directory
Step 1. After launching the MSI click âNextâ

Step 2. Tick âI accept the terms in the Licence Agreementâ and click âNextâ
Step 2. 3lick âNextâ
Step 4. Click âNextâ
Note: By ticking the âChange PowerShell execution policy from âRestrictedâ to âAllSignedâ you are relaxing the execution policy of PowerShell. However you will still need to turn this off entirely for the testing of your script.
Step 5. Click âInstallâ
Step 6. Click âFinishâ
You have now successfully install the Quest ActiveRoles Management Shell for Active Directory. Now it is time to use the new PowerShell Command.
Running the add-QADPermission PowerShell command
Step 1. To run the add-QADPermissions PowerShell command click on the PowerShell shortcut (that blue one in the taskbar if you are running 2008/R2).
Step 2. Run the command the following command to load the Quest PowerShell commands.
Add-PSSnapin Quest.ActiveRoles.ADManagement
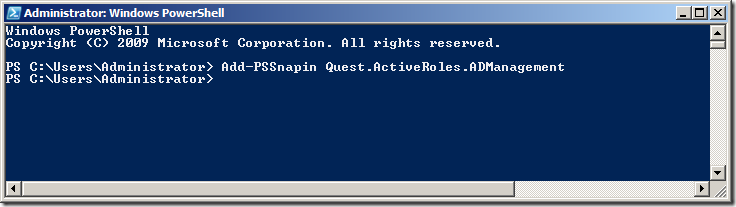
Step 3. To test that the new PSSnapin is loaded type âadd-qadperâ and then press the âTabâ key to complete the command.
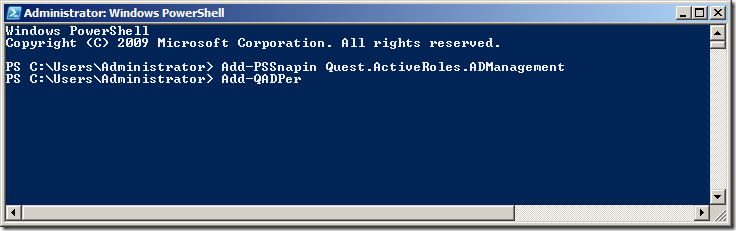
This should auto-complete the command to âAdd-QADPermissionâ
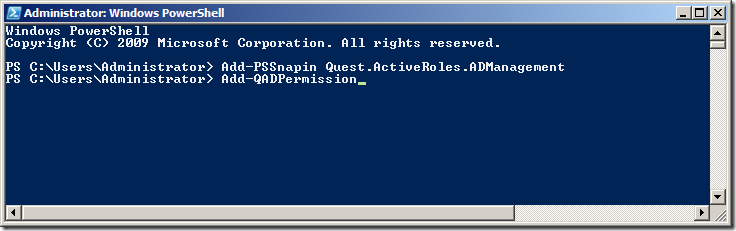
REMEMBER: Every time you launch a new PowerShell window you are going to need to run âAdd-PSSnapin Quest.ActiveRoles.ADManagementâ to load to load the Quest PowerShell Snapinâs otherwise you will see a message like the image below.
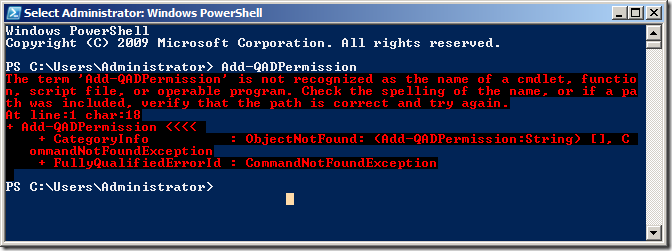
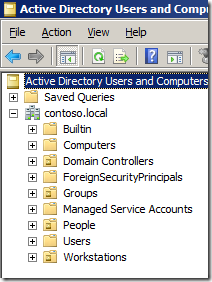
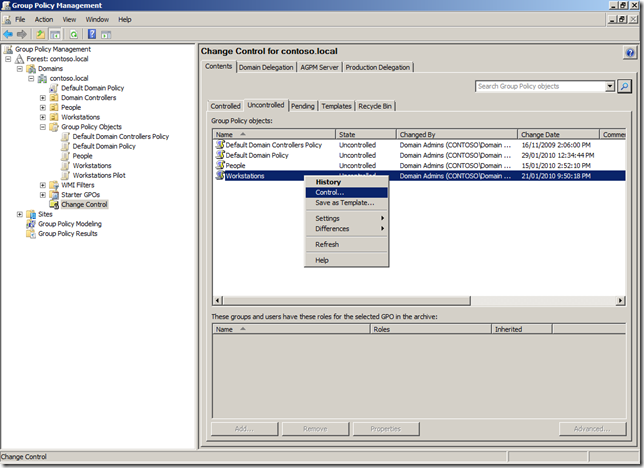
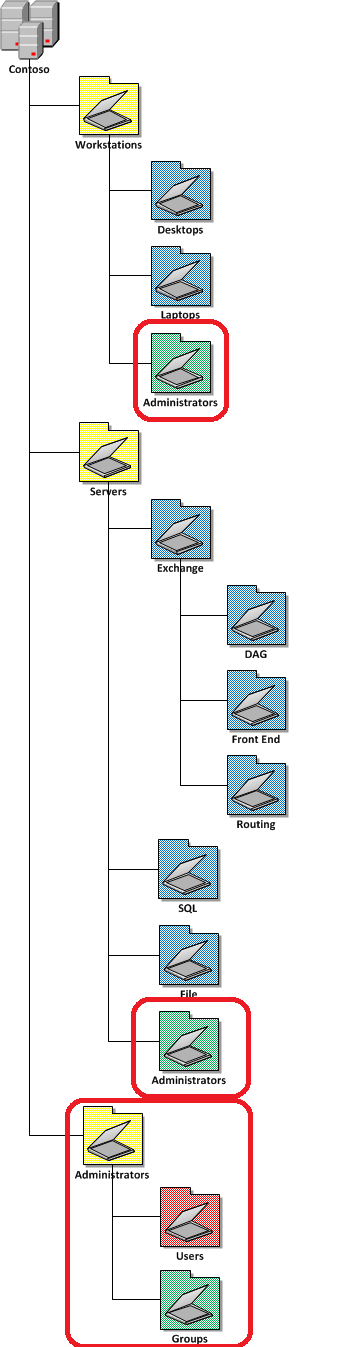
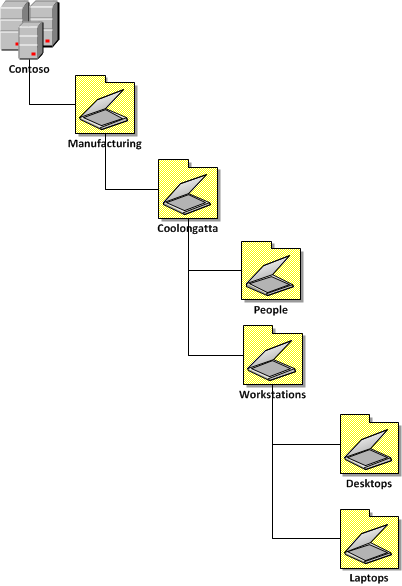
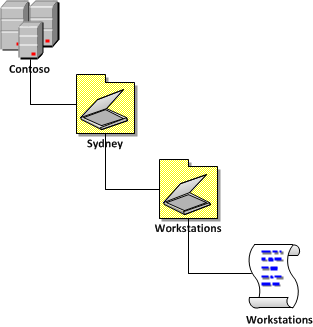
Now that we have verified that the new Quest AD PowerShell commands lets take a look at the command that will replicate some of the common tasks in the âDelegation of Control Wizardâ. In our example environment that we have an AD with three top level OUâs called âPeopleâ âGroupsâ and âWorkstationsâ (see below). These OU only contain the same type of objects that match the name of the OU (e.g. âPeopleâ contains User AD Objects) but it is possible to delegate all the permissions to the same single OU if it contains objects of multiple types (e.g. user,computers and groups).
Delegating Create, delete and manage user accounts permissions using add-QADPermission
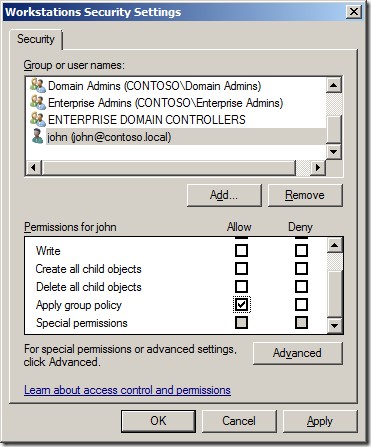
To delegate the same permission as the âCreate, delete, and mange user accountsâ (effectively Full Control) option in the âDelegation of Control Wizardâ (see below) you need to delegate two permissions to the OU.
- Allow access to all the properties of the user objects
- Create / Delete permission of the user object
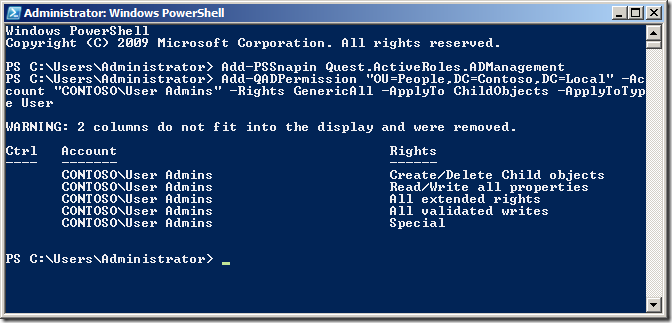
The first command will delegate Allow access to all the properties to the group called âUser Adminsâ to all User objects in the OU with the distinguished name of âOU=People,DC=Contoso,DC=Localâ.
Add-QADPermission âOU=People,DC=Contoso,DC=Localâ âAccount âCONTOSOUser Adminsâ -Rights GenericAll -ApplyTo ChildObjects -ApplyToType User
The second command will delegate Create / Delete permission for the User objects to the same OU for the same group.
Add-QADPermission âOU=People,DC=Contoso,DC=Localâ -Account âCONTOSOUser Adminsâ -Rights CreateChild,DeleteChild -ApplyTo All -ChildType User
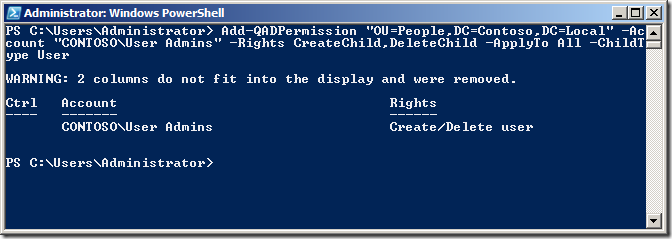
Now we can check the security on the People OU in Active Directory Users and Computer to verify the permission has been added correctly.
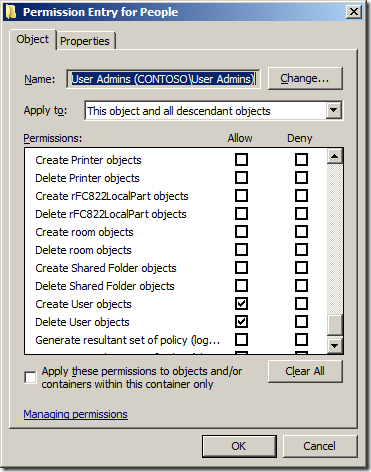
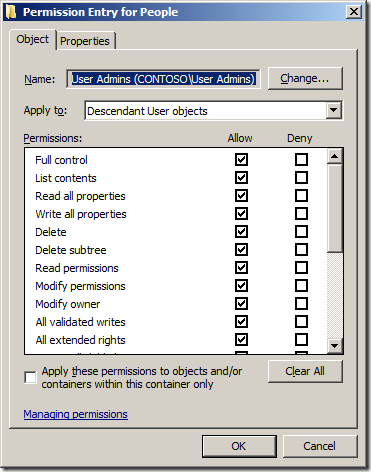
Note: See how we have used the â-ApplyTo ChildObjectsâ parameter and the âApplyTo Allâ to ensure that these permission will inherit to all objects in this OU and sub-OUâs.
If the OU that you want to give the same Full Control permission to a Computers or Groups AD Object type all you need to do is change the -ApplyToType and -ChildType parameter to âcomputerâ or âgroupâ (See examples below)
Example delegation Create, delete and manage (a.k.a. Full Control) Groups permissions using add-QADPermission
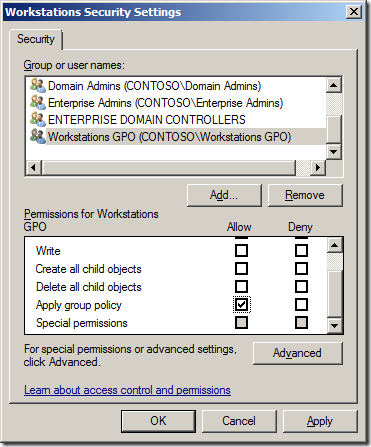
Add-QADPermission âOU=Workstations,DC=Contoso,DC=Localâ âAccount âCONTOSOWorkstations Adminsâ -Rights GenericAll -ApplyTo ChildObjects -ApplyToType Computer
Add-QADPermission âOU=Workstations,DC=Contoso,DC=Localâ -Account âCONTOSOWorkstations Adminsâ -Rights CreateChild,DeleteChild -ApplyTo All -ChildType Computer
Example delegation Create, delete and manage (a.k.a. Full Control) Computers permissions using add-QADPermission
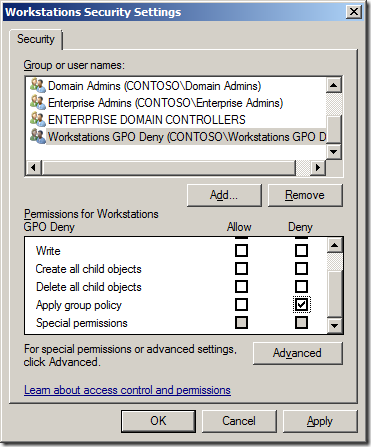
Add-QADPermission âOU=Groups,DC=Contoso,DC=Localâ âAccount âCONTOSOGroups Adminsâ -Rights GenericAll -ApplyTo ChildObjects -ApplyToType Group
Add-QADPermission âOU=Groups,DC=Contoso,DC=Localâ -Account âCONTOSOGroups Adminsâ -Rights CreateChild,DeleteChild -ApplyTo All -ChildType Group
Delegating Reset user passwords and force password change at next logon using add-QADPermission
To delegate the same permission as the âReset user passwords and force password change at next logonâ option in the âDelegation of Control Wizardâ (see below) you again need to delegate two permissions to the OU.
![image[48] image[48]](image48_thumb.png)
- Allow Read/Write to the Password Last Set Attribute
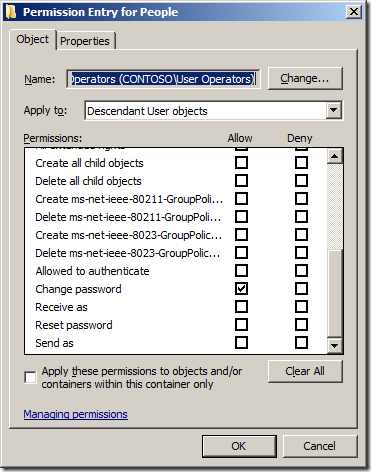
- Allow access to the "User-Change-Passwordâ Extended Right
In this example we are going to delegate Allow Read and Write permission to the Pwd-Last-Set Attribute to all User objects to the OU with the distinguished name of âOU=People,DC=Contoso,DC=Localâ to the group called âUser Operatorsâ.
Add-QADPermission âOU=People,DC=Contoso,DC=Localâ -Account âCONTOSOUser Operatorsâ -Rights ReadProperty,WriteProperty -Property ('PwdLastSet') -ApplyTo ChildObjects -ApplyToType User
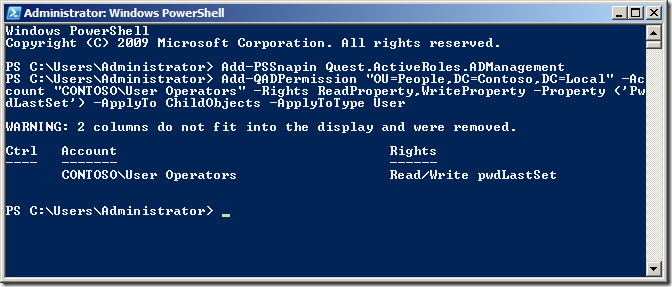
Now we are going to delegate permissions to the Extended Right User-Change-Password for the User objects to the same OU for the same group.
Add-QADPermission âOU=People,DC=Contoso,DC=Localâ -Account âCONTOSOUser Operatorsâ -ExtendedRight User-Change-Password -ApplyTo ChildObjects -ApplyToType User
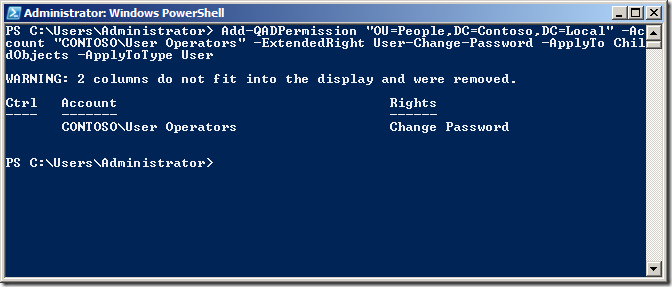
Again check the security on the People OU in Active Directory Users and Computer to verify the permission has been added correctly.
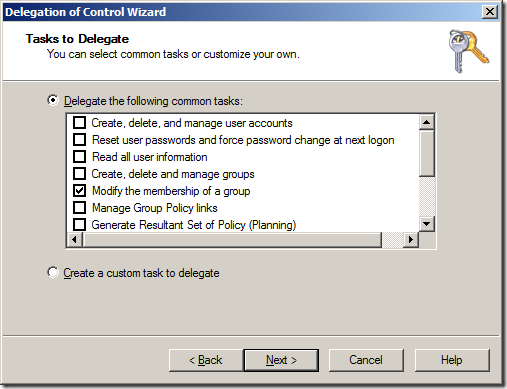
Delegating Modify the membership of a group using add-QADPermission
To delegate the same permission as the âModify the membership of a groupâ option in the âDelegation of Control Wizardâ (see below) you only need to apply one command to delegate the appropriate permissions.
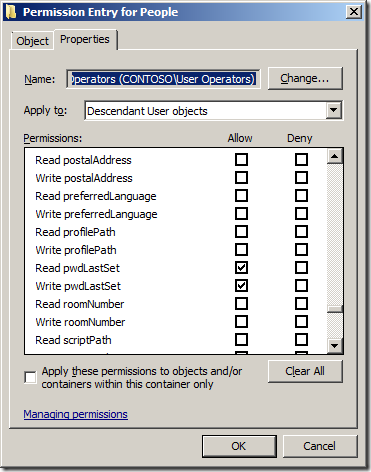
- Allow access to the Read/Write Members property on the Group
In this example we are going to delegate Change group membership permissions on all the Group objects to the OU with the distinguished name of âOU=Groups,DC=Contoso,DC=Localâ to the group called âGroup Operatorsâ
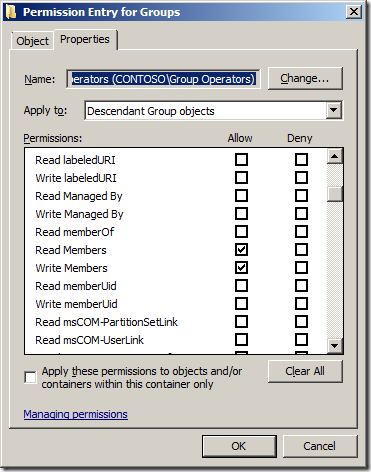
Add-QADPermission âOU=Groups,DC=Contoso,DC=Localâ -Account âCONTOSOGroup Operatorsâ -Rights ReadProperty,WriteProperty -Property ('member') -ApplyTo ChildObjects -ApplyToType Group
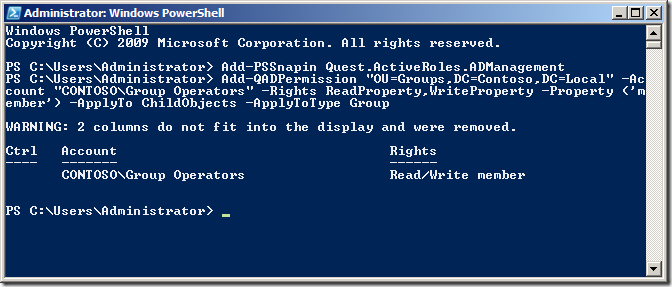
As always check the security on the People OU in Active Directory Users and Computer to verify the permission has been added correctly.
Summary
When used with the other out of the box AD PowerShell commands you should now be able to fully automate the creation AND delegation of permissions to a new OU structure for your environment.
References Sites
Below are some useful links to pages that show you how to use PowerShell when working with Active Directory.
- Automating Group Policy Management with Windows PowerShell
- PowerShell Get-ADUserGroupMembership
- Group Policy Team Blog: Group Policy & Scripting
- Group Policy Team Blog: PowerShell Script with GP cmdlets: Registry setting, Link
- TechNet: Active Directory Administration with Windows PowerShell
- MSDN Blog: Extending Active Directory Powershell
- The Experts Community: Delegating the PowerShell Way
Other AD Security Related Pages
- TechNet: Access control in Active Directory
- TechNet: Delegating administration
- TechNet: Delegate Control of an Organizational Unit
How to make Adobe Reader more secure using Group Policy
Update: I have since reposted this article with new registry keys that makes configured Adobe updater a lot easer. Check it out at  http://www.grouppolicy.biz/2010/06/updated-how-to-make-adobe-reader-more-secure-using-group-policy/
Recently there have been a number of critical security issues that have been associated with Adobe Reader (see below).
- http://securitygarden.blogspot.com/2010/04/critical-adobe-and-adobe-acrobat-update.html
- http://securitygarden.blogspot.com/2010/01/adobe-readeracrobat-critical-update.html
- http://securitygarden.blogspot.com/2009/10/adobe-reader-and-acrobat-critical.html
- http://securitygarden.blogspot.com/2009/05/critical-update-adobe-reader-and.html
- http://securitygarden.blogspot.com/2009/12/critical-adobe-pdf-vulnerability.html
- http://securitygarden.blogspot.com/2010/01/adobe-readeracrobat-critical-update.html
- http://www.adobe.com/support/security/advisories/apsa09-07.html
To see a complete list of current updates for Adobe Reader (all current versions) on Windows go to http://www.adobe.com/support/downloads/product.jsp?product=10&platform=Windows
This has has left IT administrators with a bit of a nightmare as to how to keep Reader secure as Adobe donât have the wonderful tools such as Group Policy and Windows Update, WSUS and SCCM to manage their patch rollout deployment.
One thing you might notice about the many of the vulnerabilities in Adobe products is that they are frequently JavaScript issues. Surprisingly the recommend action from Adobe to mitigate this security issues is to simply turn off JavaScript (which is enabled by default) in Adobe Reader. Seeing how rarely the JavaScript option is actually used in Adobe Reader I recommend that you just configure this option to be permanently turned off (see image 1).
Image 1. Adobe Reader JavaScript option
Disabling JavaScript
Now there is no way to disable the user interface you can disable the user interface using third-party tools (see http://www.policypak.com/support-and-sharing/video-tutorials) to prevent users to re-enabling this option. However some users might need to open PDFâs with JavaScript content so leaving the UI enabled would allow them to re-enable the option when needed. The good thing about configuring this registry key via Group Policy Preferences is that it would automatically turn the option off in the background at the next policy update leaving JavaScript only enabled for a few hours. NICE!
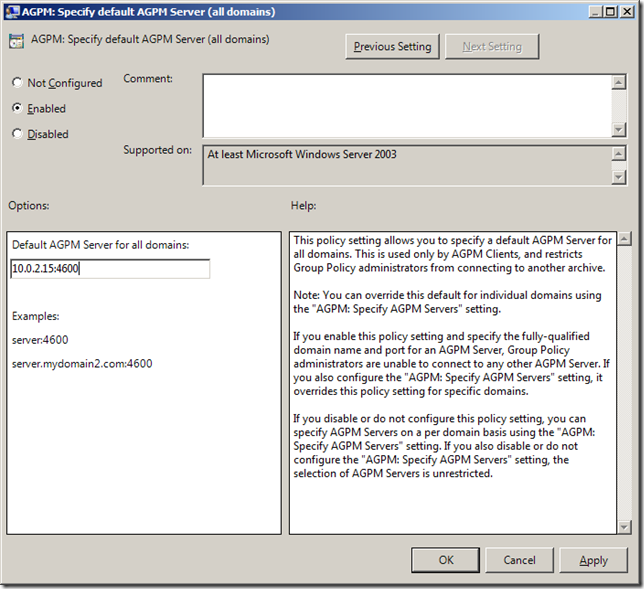
To do disable this option edit a Group Policy Object (GPO) that is targeted to the users accounts. Once you have opened the GPO in the Group Policy Management Editor go to User Configuration > Preferences > Windows Settings > Registry then go to Action > All Tasks > Add and configured a New Registry setting (as per image below).
Image 2. Disable JavaScript registry key
The key to update is:
Key: HKCUSoftwareAdobeAcrobat Reader9.0JSPrefs
Value: bEnableJS (REG_DWORD)
Data: 0 (zero)
Note: If you donât want this option to be turned off once a users has re-enabled it then tick the âApply once and do not reapplyâ option in the âCommonâ tab (see image 3) as this will only change this registry key once making it more a default setting rather then an enforced one.
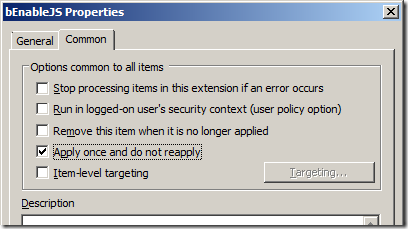
Image 3. Apply one and do not reapply
Configuring Automatic Update for Adobe Reader
Adobe has also added a âAutomatically install updatesâ feature (see image 4) with the release of Adobe Reader 9.2.0. however as of the time of writing this document the new version of Adobe Reader 9.3.0 is out and for some reason it is not automatically updating. So maybe there is a little more work to go here for Adobe.
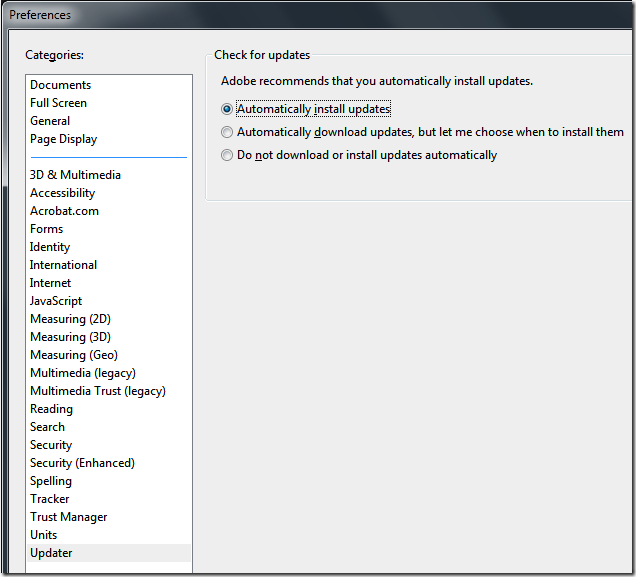
Image 4. Adobe Reader Updater Preferences
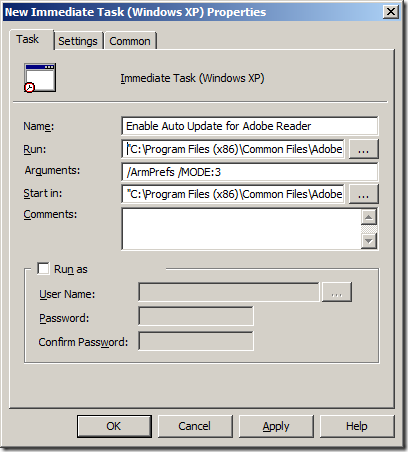
If you do want to experiment with configuring this option via group policy then you need to run the following command on the computer in the context of the system account.
âC:Program FilesCommon FilesAdobeARM1.0ReaderUpdater.exeâ /ArmPrefs /MODE:3
Note: You need to use âProgram Files (x86)â if you are running 64bit version of Windows.
You can do this my using the âNew Immediate Taskâ option under Computer Configuration > Preferences > Control Panel Settings > Scheduled Tasks in the Group Policy Management Editor.
Â
So good luck with trying securing Adobe Reader in your organisation as its certainly a front that IT administrator need to focus more upon as McAfee labs have said âAdobe product exploitation will likely surpass that of Microsoft Office applications in 2010.â.
How to delegate AD permission to Organisational Units using the PowerShell command Add-QADPermission
Recently, I have been working a lot with PowerShell to automate the creation of a full AD site OU structure (with Group Policy and all) along with all the necessary delegated permissions. One of the limitation of the out of the box AD PowerShell commands is there is no easy way (but apparently there is a really hard way) to delegate permission to Active Directory OUâs. Luckily Quest Software have helped a lot here and they have offered a set of FREE PowerShell commands for Active Directory called âActiveRoles Management Shell for Active Directoryâ one of which is called Add-QADPermission which greatly simplifies the process of delegation security in AD.
The Add-QADPermission command can be used to add an DACL security descriptor permission to any AD object with a distinguished name such as users, computer or OUâs. Therefore you can use this to delegate permission to OU similarly to running a âDelegation of Control Wizardâ in Active Directory Users and Computers console (see image below).
This wizard allows you to delegate some common tasks (see below) to your OUâs in you Active Directory however the permissions they apply are not straight forward simple permissions.
 |
 |
What I will show you how to do is how to perform some of the common delegation tasks that the âDelegation of Control Wizardâ using a PowerShell command so you can automate the process for creating new OUâs in your environment. I know this is not strictly an Group Policy topic but it is one closely related and one I think many Group Policy admins will find useful.
The Command tasks I will show you are the oneâs that I almost exclusively use when delegating permissions to Active Directory, they are:
- Create, delete and manage user accounts
- and Groups
- and Computers
- Reset user passwords and force password change at next logon
- Modify the membership of a group
Getting started â Installing the ActiveRoles Management Shell for Active Directory
The Add-QADPermission command is a third party PowerShell command so you will need to first download and install the new commands from the Quest site on the computer that you will be running the PowerShell commands. You can download the Quest ActiveRoles Management Shell for Active Directory from here http://www.quest.com/PowerShell/activeroles-server.aspx and then install the MSI file.
Installing ActiveRoles Management Shell for Active Directory
Step 1. After launching the MSI click âNextâ

Step 2. Tick âI accept the terms in the Licence Agreementâ and click âNextâ

Step 2. 3lick âNextâ

Step 4. Click âNextâ
Note: By ticking the âChange PowerShell execution policy from âRestrictedâ to âAllSignedâ you are relaxing the execution policy of PowerShell. However you will still need to turn this off entirely for the testing of your script.

Step 5. Click âInstallâ

Step 6. Click âFinishâ

You have now successfully install the Quest ActiveRoles Management Shell for Active Directory. Now it is time to use the new PowerShell Command.
Running the add-QADPermission PowerShell command
Step 1. To run the add-QADPermissions PowerShell command click on the PowerShell shortcut (that blue one in the taskbar if you are running 2008/R2).

Step 2. Run the command the following command to load the Quest PowerShell commands.
Add-PSSnapin Quest.ActiveRoles.ADManagement

Step 3. To test that the new PSSnapin is loaded type âadd-qadperâ and then press the âTabâ key to complete the command.

This should auto-complete the command to âAdd-QADPermissionâ

REMEMBER: Every time you launch a new PowerShell window you are going to need to run âAdd-PSSnapin Quest.ActiveRoles.ADManagementâ to load to load the Quest PowerShell Snapinâs otherwise you will see a message like the image below.

Now that we have verified that the new Quest AD PowerShell commands lets take a look at the command that will replicate some of the common tasks in the âDelegation of Control Wizardâ. In our example environment that we have an AD with three top level OUâs called âPeopleâ âGroupsâ and âWorkstationsâ (see below). These OU only contain the same type of objects that match the name of the OU (e.g. âPeopleâ contains User AD Objects) but it is possible to delegate all the permissions to the same single OU if it contains objects of multiple types (e.g. user,computers and groups).

Delegating Create, delete and manage user accounts permissions using add-QADPermission
To delegate the same permission as the âCreate, delete, and mange user accountsâ (effectively Full Control) option in the âDelegation of Control Wizardâ (see below) you need to delegate two permissions to the OU.

- Allow access to all the properties of the user objects
- Create / Delete permission of the user object
The first command will delegate Allow access to all the properties to the group called âUser Adminsâ to all User objects in the OU with the distinguished name of âOU=People,DC=Contoso,DC=Localâ.
Add-QADPermission âOU=People,DC=Contoso,DC=Localâ âAccount âCONTOSOUser Adminsâ -Rights GenericAll -ApplyTo ChildObjects -ApplyToType User

The second command will delegate Create / Delete permission for the User objects to the same OU for the same group.
Add-QADPermission âOU=People,DC=Contoso,DC=Localâ -Account âCONTOSOUser Adminsâ -Rights CreateChild,DeleteChild -ApplyTo All -ChildType User

Now we can check the security on the People OU in Active Directory Users and Computer to verify the permission has been added correctly.


Note: See how we have used the â-ApplyTo ChildObjectsâ parameter and the âApplyTo Allâ to ensure that these permission will inherit to all objects in this OU and sub-OUâs.
If the OU that you want to give the same Full Control permission to a Computers or Groups AD Object type all you need to do is change the -ApplyToType and -ChildType parameter to âcomputerâ or âgroupâ (See examples below)
Example delegation Create, delete and manage (a.k.a. Full Control) Groups permissions using add-QADPermission
Add-QADPermission âOU=Workstations,DC=Contoso,DC=Localâ âAccount âCONTOSOWorkstations Adminsâ -Rights GenericAll -ApplyTo ChildObjects -ApplyToType Computer
Add-QADPermission âOU=Workstations,DC=Contoso,DC=Localâ -Account âCONTOSOWorkstations Adminsâ -Rights CreateChild,DeleteChild -ApplyTo All -ChildType Computer
Example delegation Create, delete and manage (a.k.a. Full Control) Computers permissions using add-QADPermission
Add-QADPermission âOU=Groups,DC=Contoso,DC=Localâ âAccount âCONTOSOGroups Adminsâ -Rights GenericAll -ApplyTo ChildObjects -ApplyToType Group
Add-QADPermission âOU=Groups,DC=Contoso,DC=Localâ -Account âCONTOSOGroups Adminsâ -Rights CreateChild,DeleteChild -ApplyTo All -ChildType Group
Delegating Reset user passwords and force password change at next logon using add-QADPermission
To delegate the same permission as the âReset user passwords and force password change at next logonâ option in the âDelegation of Control Wizardâ (see below) you again need to delegate two permissions to the OU.
![image[48] image[48]](image48_thumb.png)
- Allow Read/Write to the Password Last Set Attribute
- Allow access to the "User-Change-Passwordâ Extended Right
In this example we are going to delegate Allow Read and Write permission to the Pwd-Last-Set Attribute to all User objects to the OU with the distinguished name of âOU=People,DC=Contoso,DC=Localâ to the group called âUser Operatorsâ.
Add-QADPermission âOU=People,DC=Contoso,DC=Localâ -Account âCONTOSOUser Operatorsâ -Rights ReadProperty,WriteProperty -Property ('PwdLastSet') -ApplyTo ChildObjects -ApplyToType User

Now we are going to delegate permissions to the Extended Right User-Change-Password for the User objects to the same OU for the same group.
Add-QADPermission âOU=People,DC=Contoso,DC=Localâ -Account âCONTOSOUser Operatorsâ -ExtendedRight User-Change-Password -ApplyTo ChildObjects -ApplyToType User

Again check the security on the People OU in Active Directory Users and Computer to verify the permission has been added correctly.


Delegating Modify the membership of a group using add-QADPermission
To delegate the same permission as the âModify the membership of a groupâ option in the âDelegation of Control Wizardâ (see below) you only need to apply one command to delegate the appropriate permissions.

- Allow access to the Read/Write Members property on the Group
In this example we are going to delegate Change group membership permissions on all the Group objects to the OU with the distinguished name of âOU=Groups,DC=Contoso,DC=Localâ to the group called âGroup Operatorsâ
Add-QADPermission âOU=Groups,DC=Contoso,DC=Localâ -Account âCONTOSOGroup Operatorsâ -Rights ReadProperty,WriteProperty -Property ('member') -ApplyTo ChildObjects -ApplyToType Group

As always check the security on the People OU in Active Directory Users and Computer to verify the permission has been added correctly.

Summary
When used with the other out of the box AD PowerShell commands you should now be able to fully automate the creation AND delegation of permissions to a new OU structure for your environment.
References Sites
Below are some useful links to pages that show you how to use PowerShell when working with Active Directory.
- Automating Group Policy Management with Windows PowerShell
- PowerShell Get-ADUserGroupMembership
- Group Policy Team Blog: Group Policy & Scripting
- Group Policy Team Blog: PowerShell Script with GP cmdlets: Registry setting, Link
- TechNet: Active Directory Administration with Windows PowerShell
- MSDN Blog: Extending Active Directory Powershell
- The Experts Community: Delegating the PowerShell Way
Other AD Security Related Pages
- TechNet: Access control in Active Directory
- TechNet: Delegating administration
- TechNet: Delegate Control of an Organizational Unit






![image[23] image[23]](image23_thumb.png)
![image[21] image[21]](image21_thumb.png)
![image[30] image[30]](image30_thumb1.png)
![image[62] image[62]](image62_thumb1.png)
![image[39] image[39]](image39_thumb1.png)