There is currently a security advisory out about a Zero Day vulnerability in Internet Explore 6 & 7 on Windows XP and Vista. While there is no patch out for this issues so far you can mitigate the security a number ways using Group Policy. Below I have listed two ways to implement the workaround as listed by Microsoft using Group Policy.
Method 1. Modify the Access Control List (ACL) on iepeers.dll
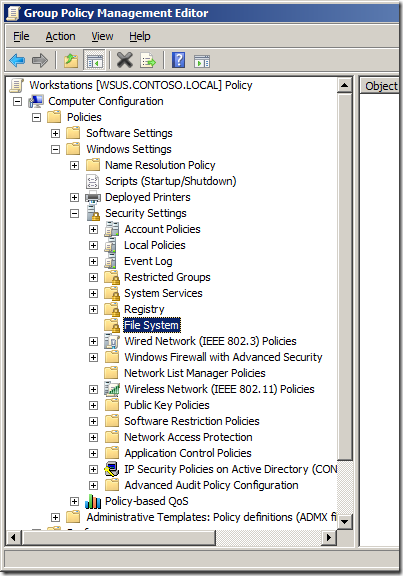
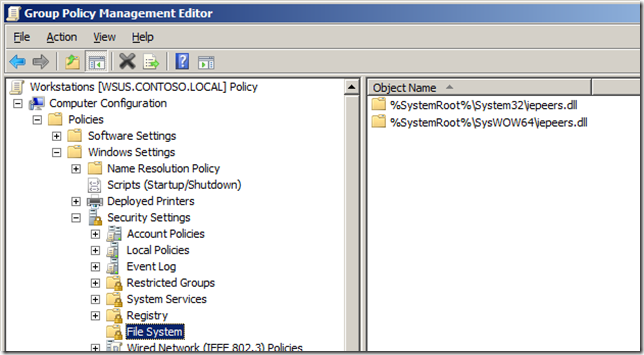
Step 1. Edit a Group Policy Object (GPO) that is targeted to the computer accounts you want to apply this setting. Then navigate to Computer Configurations > Windows Settings > Security Settings > File System.
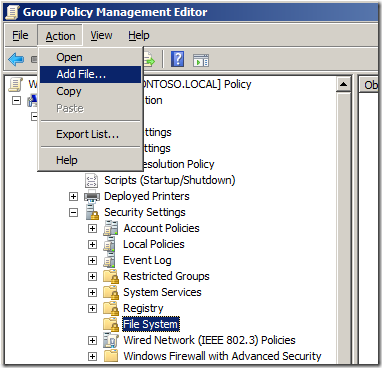
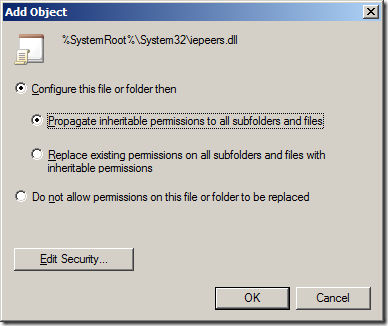
Step 2. Click on “Action†in the menu and then “Add File…â€
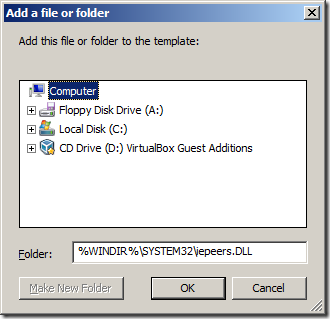
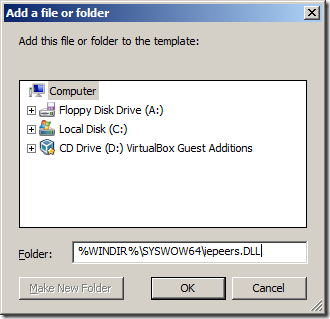
Step 3. Type “%WINDIR%\System32\iepeers.DLL†into the Folder: field then click “OKâ€
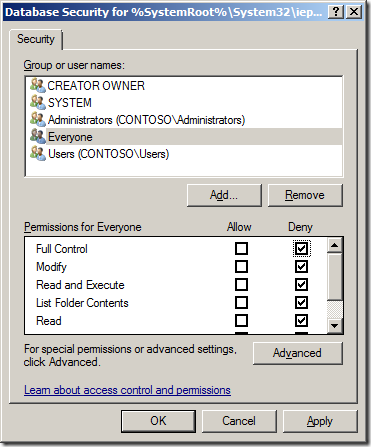
Step 4. Click “Addâ€and then add the “Everyone†group and click “OKâ€
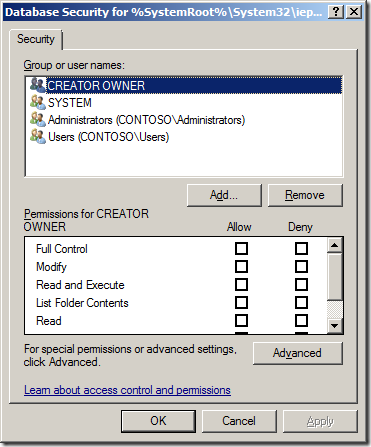
Step 5. Tick the Full Control “Deny†tick box. This will then tick all the Deny tick boxes.
Step 6. Click “Yes†to the Deny warning.
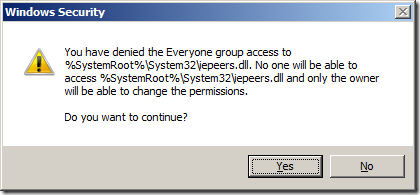
Step 7. Click “OK†to the permissions option.
Note: If you want to apply this to x64 version of Windows as well repeat step 2 thought 7 but type “%WINDIR%\SYSWOW64\iepeers.DLL†instead in the Folder: field.
You have now denied permissions to the file that has the issues.
Once you have applied the patch to fix this vulnerability be sure to go into each of file security settings and remove the “Everyone†deny permission from the setting.
Method 2: Configure Internet Explorer to prompt before running Active Scripting or to disable Active Scripting in the Internet and Local intranet security zone
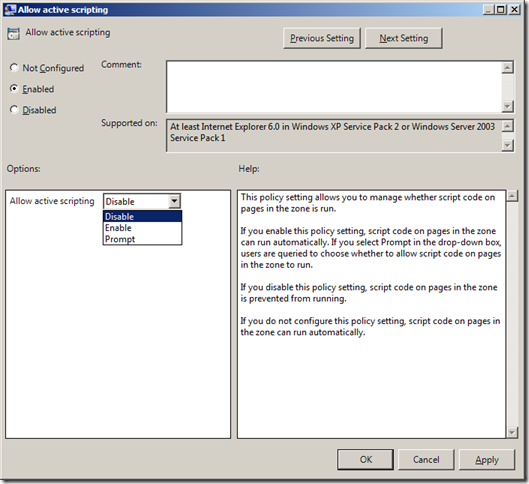
Step 1. Edit a GPO that is targeted to the users accounts you want to apply security setting. Then Enabled both the “Allow active scripting†under User Configuration > Policies > Administrative Templates > Windows Components > Internet Explorer > Security Page > Internet Zone and the Intranet Zone. Then configure the Options to either “Prompt†or “Disableâ€.
Once you have performed the above configuration changes be sure to add *.windowsupdate.microsoft.com, *.update.microsoft.com and any other site you require to run Active Scripting on to the trusted sites zone list. Instructions on how to do this can be found here How to use Group Policy to configure Internet Explorer security zone sites
Disclaimer: I do not guarantee that this information will work. All the above information is to be used at your own risk.
For more details on the security vulnerability and other ways to mitigate this issue see Microsoft Security Advisory (981374)




Blog Post: How to use Group Policy to mitigate security issue KB981374 http://bit.ly/cku7IA
How to use Group Policy to mitigate security issue KB981374 http://bit.ly/cku7IA
RT @grouppolicy_biz: Blog Post: How to use Group Policy to mitigate security issue KB981374 http://bit.ly/cku7IA
How to use Group Policy to mitigate security issue KB981374 http://ow.ly/1qtFTg
There is a fix for this since March 30, 2010.
MS10-018 issued KB980182 which resolves this issue.
you should update the header of this article.