Update 2: Adobe has now published an official Group Policy Administrative template that has a pre-configured setting to disable Java Script. Check out my ne blog post How to configure Group Policy for Adobe Reader XIÂ for instructions.
Update: This article is a re-publish of a post I have previously posted. This time I have updated the “Configuring Automatic Update for Adobe Reader†section below with now an officially documented and more reliable method. I have also added a section called “Locking down the Automatic Update option for Adobe Reader†which shows you how to prevent users from changing Adobe Reader update options once they are configured.
Recently there have been a number of critical security issues that have been associated with Adobe Reader (see below).
- http://securitygarden.blogspot.com/2010/06/security-advisory-adobe-flash-player.html
- http://securitygarden.blogspot.com/2010/04/critical-adobe-and-adobe-acrobat-update.html
- http://securitygarden.blogspot.com/2010/01/adobe-readeracrobat-critical-update.html
- http://securitygarden.blogspot.com/2009/10/adobe-reader-and-acrobat-critical.html
- http://securitygarden.blogspot.com/2009/05/critical-update-adobe-reader-and.html
- http://securitygarden.blogspot.com/2009/12/critical-adobe-pdf-vulnerability.html
- http://securitygarden.blogspot.com/2010/01/adobe-readeracrobat-critical-update.html
- http://www.adobe.com/support/security/advisories/apsa09-07.html
New: To see a complete list of current updates for Adobe Reader (all current versions) on Windows go to http://www.adobe.com/support/downloads/product.jsp?product=10&platform=Windows
This has has left IT administrators with a bit of a nightmare as to how to keep Reader secure as Adobe don’t have the wonderful tools such as Group Policy and Windows Update, WSUS and SCCM to manage their patch rollout deployment.
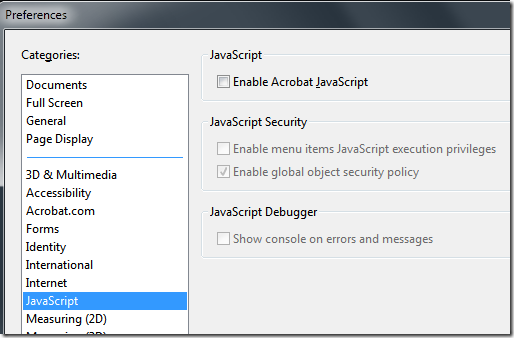
One thing you might notice about the many of the vulnerabilities in Adobe products is that they are frequently JavaScript issues. Surprisingly the recommend action from Adobe to mitigate this security issues is to simply turn off JavaScript (which is enabled by default) in Adobe Reader. Seeing how rarely the JavaScript option is actually used in Adobe Reader I recommend that you just configure this option to be permanently turned off (see image 1).
Image 1. Adobe Reader JavaScript option
Disabling JavaScript
Now there is no way to disable the user interface you can disable the user interface using third-party tools (see http://www.policypak.com/support-and-sharing/video-tutorials) to prevent users to re-enabling this option. However some users might need to open PDF’s with JavaScript content so leaving the UI enabled would allow them to re-enable the option when needed. The good thing about configuring this registry key via Group Policy Preferences is that it would automatically turn the option off in the background at the next policy update leaving JavaScript only enabled for a few hours. NICE!
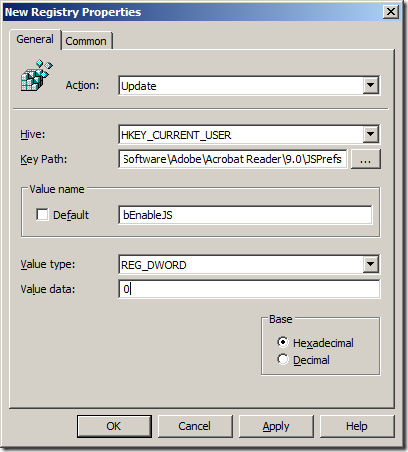
To do disable this option edit a Group Policy Object (GPO) that is targeted to the users accounts. Once you have opened the GPO in the Group Policy Management Editor go to User Configuration > Preferences > Windows Settings > Registry then go to Action > All Tasks > Add and configured a New Registry setting (as per image below).
Image 2. Disable JavaScript registry key
The key to update is:
Key: HKCU\Software\Adobe\Acrobat Reader\9.0\JSPrefs
Value:Â bEnableJS (REG_DWORD)
Data: 0 (zero)
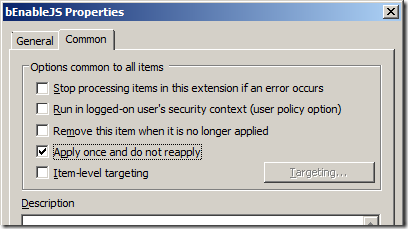
Note: If you don’t want this option to be turned off once a users has re-enabled it then tick the “Apply once and do not reapply†option in the “Common†tab (see image 3) as this will only change this registry key once making it more a default setting rather then an enforced one.
Image 3. Apply one and do not reapply
Updated: Configuring Automatic Update for Adobe Reader
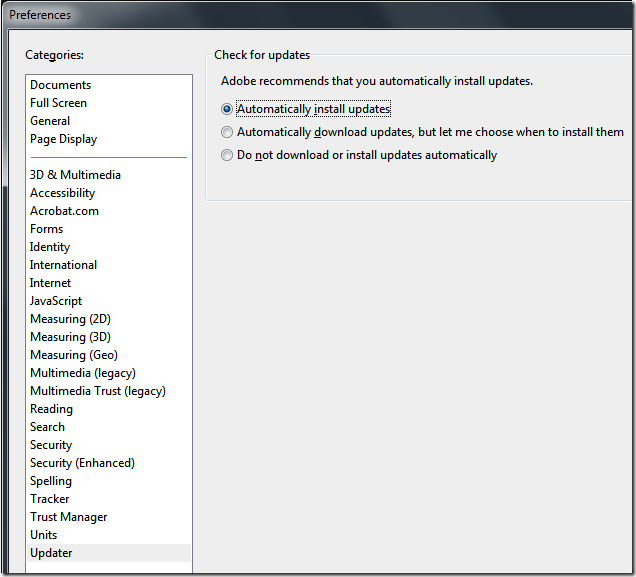
Adobe has also added a “Automatically install updates†feature (see image 4) with the release of Adobe Reader 9.2.0. however as of the time of writing this document the new version of Adobe Reader 9.3.0 is out and for some reason it is not automatically updating. So maybe there is a little more work to go here for Adobe.
Thanks to Ryan Steel for pointing out that Adobe have now published a document ( http://kb2.adobe.com/cps/837/cpsid_83709/attachments/Acrobat_Reader_Updater.pdf ) that documents the registry key for enabling the “Automatically install updates†option.
Image 4. Adobe Reader Updater Preferences
Image 5. Adobe Reader Updater System Tray Notification
Â
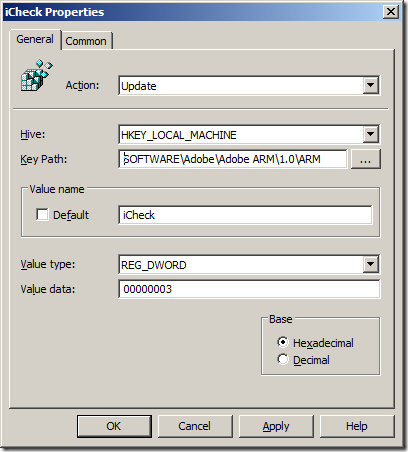
The key to configure automatic update is:
Key: HKEY_LOCAL_MACHINE\SOFTWARE\Adobe\Adobe ARM\1.0\ARM
Value:Â iCheck (REG_DWORD)
Data: 0 (Manual)
2 (Semi-Automatic)
3 (Automatic)
Below is an example of how you would configure this registry key using Group Policy Preferences. Be sure that this key is targeted to the computer object as it is a local machine setting.
Image 6. Group Policy Preferences Updater Registry Key
As Adobe digitally sign their program this means their (not-so) quarterly security update should automatically update the program without prompting normal users for a UAC elevation prompt (ref http://kb2.adobe.com/cps/838/cpsid_83813.html).
Note: Ryan did pointed out that this automatic update without a UAC prompt might not necessarily be work as expected so you will need to test this automatic update facility for your environment.
Having the program digitally signed also means that you can easily prevent any older version of the program from running using AppLocker with Windows 7. If you want to see some instruction on how to do this check out my other blog post How to configure AppLocker Group Policy in Windows 7 to block third-party browsers.
New: Locking down the Automatic Update option for Adobe Reader
Another registry key that is document in this article show the key that locks down the user interface for the Adobe Reader update option. This is very handy as if you configured Adobe Updater to Automatic then locking down the UI will make it a LOT harder for users to turn this option off.
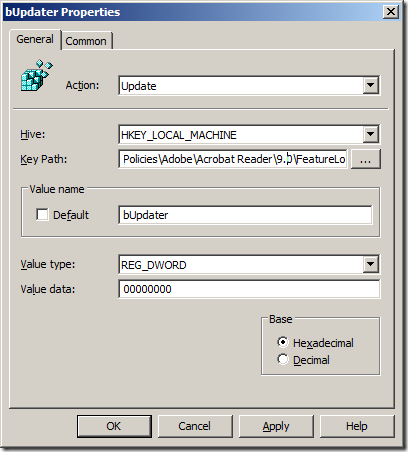
The key to lock down Adobe Updater is:
Key: HKEY_LOCAL_MACHINE\SOFTWARE\Polices\Adobe\{product}\{version}\FeatureLockdown
Value: bUpdater (REG_DWORD)
Data: 0 (Locked Down)
Note: The patch listed in the Adobe documentation for this option is wrong therefore I have added “Polices†to the key above to correct for this error.
Also note the above example has {product} and {version} which you should substitute the value “Acrobat Reader†and “9.0†(see image 7 below). You would obviously have to change the version number to match the version of Adobe Reader you have deployed in your environment.
Image 8. Group Policy Preferences lockdown updater Registry Key
Once this key is applied to your computers you will now see that the “Check for Updates†under the help menu and the “Updater†section under preferences have now been removed (see images below).
Image 9. “Check for Update†removed from help menu
Image 10. “Updater†removed from Preferences
While most IT professional don’t like having to install Adobe Reader in their environment at least this will certainly go a long way to making it as secure as possible. It would certainly seem that McAfee labs predictions have come true (“Adobe product exploitation will likely surpass that of Microsoft Office applications in 2010.â€) as Steve Gibson (founder of the Gibson Research Corporation) mentioned on his latest Security Now podcast that Adobe are now looking at changing to a monthly security patching cycle as they are continuity having to release emergency out of cycles patches any way.
Good Luck!!!




Blog Post: Updated: How to make Adobe Reader more secure using Group Policy http://bit.ly/ct3j3H
Blog Post: How to make Adobe Reader more secure using Group Policy http://bit.ly/ct3j3H #mvpbuzz
RT @grouppolicy_biz: Blog Post: Updated: How to make Adobe Reader more secure using Group Policy http://bit.ly/ct3j3H
How to make Adobe Reader more secure using Group Policy http://bit.ly/9bGLve
RT @alanburchill: How to make Adobe Reader more secure using Group Policy http://bit.ly/9bGLve
RT @markwilsonit: RT @alanburchill: How to make Adobe Reader more secure using Group Policy http://bit.ly/9bGLve <GPO to remove & add Foxit?
Great article.
I was going to make an admx file to control these adobe reader settings and had trouble tracking down the relevant reg keys but this article has really helped, thanks 🙂
Excellent post, thanks Alan!
Been going through the AIM for acrobat (http://kb2.adobe.com/cps/837/cpsid_83709.html) documents and realised that JS appears to be the tip of a rapidly forming iceberg.
bAllowPasswordSaving, By default, password caching is turned on. I have no idea where it stores the password file, it is a SHA-1 hash by default.
ADBC, (Acrobat Database Connectivity) is a Javascript object inside of Acrobat that allows you to connect to Windows ODBC (Open Database Connectivity) data sources. Enabled by default in version 7, even if JScript is turned off.
Attachments, not locked down, run executables?
the ability for acrobat to open a file or url or even a menu item embedded as an embedded link in a document, whilst you do get a warning, I cannot see how you can turn this off.
Thats even before looking at the other issues from a corporate point of view, like acrobat.com and the collaboration menu.
Sound like you have come to the realisation of just how in-secure Adobe Reader is… not to mention the ability to run flash from within a PDF as well…
Como hacer que Adobe Reader sea más seguro… usando GPOs. http://bit.ly/bS6th2 AD Rulez!! }:))
RT @chemaalonso: Como hacer que Adobe Reader sea más seguro… usando GPOs. http://bit.ly/bS6th2 AD Rulez!! }:))
RT @chemaalonso: Como hacer que Adobe Reader sea más seguro… usando GPOs. http://bit.ly/bS6th2 AD Rulez!! }:))
RT @holesec: RT @chemaalonso: Como hacer que Adobe Reader sea más seguro… usando GPOs. http://bit.ly/bS6th2 AD Rulez!! }:))
Como hacer que Adobe Reader sea más seguro… usando GPOs. http://bit.ly/bS6th2 AD Rulez!! }:)) (via @chemaalonso)
How to disable JScript in Adobe Reader to mitigate current zero day exploit http://t.co/orLgpAi
I’ve just deployed Adobe Reader X in our environment and have found this article very informative. I do however have one issue and that is that although I’ve added HKEY_LOCAL_MACHINE\SOFTWARE\Adobe\Adobe ARM\1.0\ARM iCheck 3 (it appears in the registry as it should on all machines) I’m not sure it works. If I go to Edit\Preferences\Updater, the second option is selected: “Automatically download updates, but let me choose when to install them”.
I’ve targeted it at a computer object. Any ideas how to fix this, where there any changes in 10.x?
Hmm… not sure… but i am rolling out Adobe Reader X soon… so i will post an update…
Not sure if this is in any way related, but I’ve noticed this (at least more frequently) on machines that had previous versions of Adobe Reader (mostly 9.x in our case) installed. With fresh machines it appears to work as advertised.
I just came across this exact problem while trying to get this to work for 11.x versions of adobe. What i found was this was not working on a 64bit machine cause the reg key is moved slightly instead of HKLM\SOFTWARE\Adobe\Adobe ARM\1.0\ARM it actually HKLM\SOFTWARE\Wow6432Node\Adobe\Adobe ARM\1.0\ARM. You can still push the settings for 32 and 64 bit machine accordingly using the item-;ve; targeting under the Common Tab. Good luck!
Since 10.1 came out I’m seeing:
Update failed
This installation is forbidden by system policy. Contact your system administrator.
Error: 1625
Automatically install updates is selected, the OS I’ve noticed this on is Win7 x64, the user can even be a local administrator, but UAC is turned on.
Any ideas how to resolve this (I’d really like for it to update on its own), has anyone noticed anything similar?
I have found that 10.0.1 has updated on a few computers automaticlly…. Not sure why your upgrade has not worked, best to hit the adobe forums…. sorry
Great article. Thanks! What about if you have an environment that has multiple versions of acrobat/reader installed and it is not convenient to create a separate OU for each version? What would happen if a preference was created for each version in your environment and applied to all machines? For example if the registry path did not exist on a machine for version 10 since it was running 9, would it ignore it or go ahead and create that registry path and value? Thank you.
Yes it should work correctly…. However you could apply item level targeting so that it would only apply the registry key if the correct .exe file is present. This way you can apply it all from the one GPO but not apply excessive registry keys…
Thanks Alan! This is real helpful. Do you know if wild cards are supported in the “key Path” field?
Thanks,
@jdm Hmm…. good question… other text fields support wildcards so if i would have to make a guese i would say yes…
@HiltonT you mean like this… http://bit.ly/ct3j3H and this http://bit.ly/gYzPVE
Ive noticed that the error: “Update failed – This installation is forbidden by system policy” can occur when Windows Updates – or other MSI installations – have finished but the system is waiting for a reboot to apply changes. Rebooting the computer will permit the Adobe updates to execute correctly.