 The below article shows you how to use Group Policy Preference to setup the registry keys on a computer so that it automatically logs onto when its turned on. While doing this is potentially huge security issue and not something I would generally recommend IT staff might want to implement on computers that are highly locked down and used for only a specific propose.
The below article shows you how to use Group Policy Preference to setup the registry keys on a computer so that it automatically logs onto when its turned on. While doing this is potentially huge security issue and not something I would generally recommend IT staff might want to implement on computers that are highly locked down and used for only a specific propose.
How to set a registry key using Group Policy Preferences
Before we begin I will show you how create the required registry keys using group policy preference. After this I will list the registry keys you need to use with the instruction below to configure automatic logon.
Step 1. Edit a Group Policy Object that is applied to the computers you want this setting applied.
WARNING: Make sure you have not applied this policy to any computers before you begin as this will obviously logon any computer that this policy is applied to automatically.
Step 2. Navigate to Computer Configuration > Preferences > Windows Settings > Registry
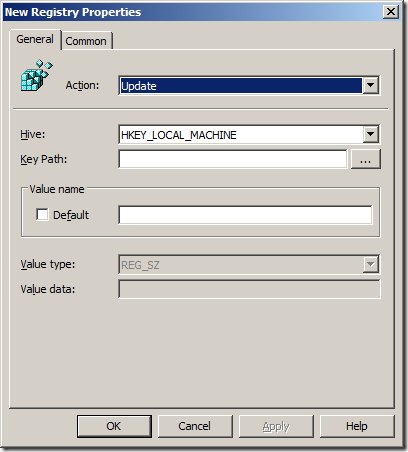
Step 3. In the Menu click on Action > New > Registry Item
Now you know how to configure a registry key setting using Group Policy Preferences you can create a new Registry Item for each registry key listed below.
How to configure Windows to automatically logon
Now we need to create the below registry keys to enable the automatic logon process.
Note: You will need to substitute you own specific values for all the text in italic below.
Enable AutoLogon
Key: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Value: AutoAdminLogon (REG_SZ)
Data: 1 (Enabled)
Default Domain Name
Key: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Value: DefaultDomainName (REG_SZ)
Data: DOMAINNAME
Default User Name
Key: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Value: DefaultUserName (REG_SZ)
Data: USERNAME
Default Password
Key: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Value: DefaultPassword (REG_SZ)
Data: PASSWORD
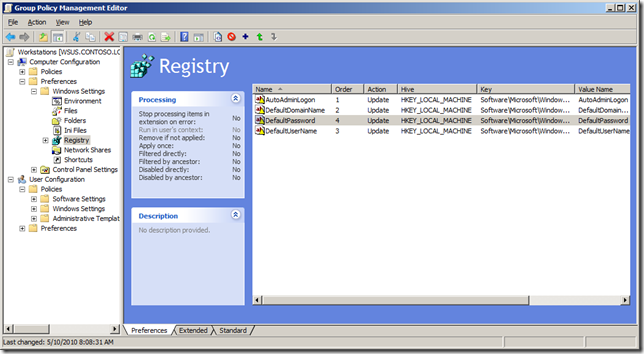
You should now have 4 registry keys configured as the image below.
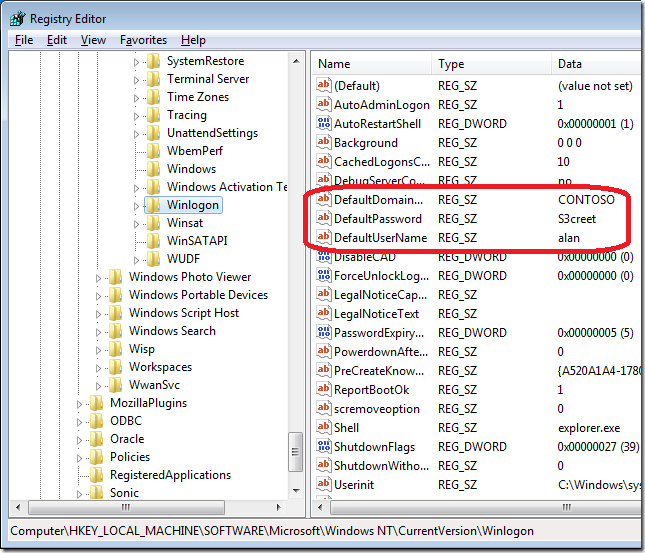
Warning: Be sure to also block the regedit tool on the user that logos onto this computer as anyone logged on the computer will be able to see the account password stored in the registry as clear text (see below).
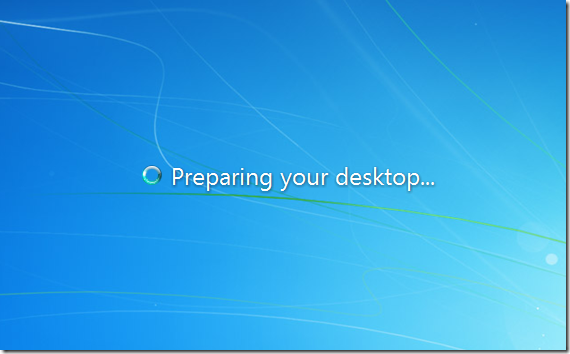
Now when ever this computer is turned on it will start up and logon automatically with the credentials that you specified in the policy (see below).




Blog Post: How to use Group Policy Preference enable auto-logon http://bit.ly/alrYTy
RT @alanburchill: Blog Post: How to use Group Policy Preference enable auto-logon http://bit.ly/alrYTy
RT @alanburchill: Blog Post: How to use Group Policy Preference enable auto-logon http://bit.ly/alrYTy
Why can’t I write to HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D} ??
This article shows several ways how to configure Windows autologon, could be useful addition for this post
Best Practice: How to use Group Policy Preference enable auto-logon http://t.co/9TTJ7p8 via @alanburchill
Hi,
I have configured a New GPO for Autologon and applied to a single computer call “AIMS” but it doesn’t work. Even I added a single user to check if it work…but no luck….
Can you please tell me best way to apply this GPO on Windows XP systems. I am using Windows 2008 32 Bit.
Regards,
Prashant
Have you pushed out Client Side extensions to the Windows XP client? This is required for GP Preferences.
No DValcourt, because I am not so sure how to do it!! Do you think that will help than please show me some guideline or link where I can see and install them.
Isn’t the AutoAdminLogon value supposed to be fo the type REG_DWORD in stead of REG_SZ ?
Hello! I was trying to follow Your instructions, but the Default Password (REG_SZ) Step 4 in the Registry is missing.
Hi , Is their any way that i can hide ,” loading user profile” message from users like VDI or Terminal access users ?
Many thanks!!!
In order to get these to work, you have to take HKLM\ off of the keys as the HIVE is already set for HKEY_LOCAL_MACHINE.
So all of the keys above should be this….
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Instead of this…
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Also, I have mine set to “Replace” and not “Update” and it works great.
I tried this method in windows 2003 server but it is not working how can i do that?
TNX Timothy Stone.
work geat!
Please correct the problems in your blog. Me and many other people have used your blog to enable autologon I would even remove the (enable) out of the blog or provide a screen shot of what it looks like in the Group Policy editor. I also used the replace instead of update I don’t know if that helped also.
Key: SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Value: AutoAdminLogon
Data: 1 (Enabled)
you should take care also of the Windows 32/64 bits version. In the latter case (64 bit) the registry keys are on another path in the registry, as stated here:
http://answers.microsoft.com/en-us/windows/forum/windows_7-security/unable-to-get-autologin-override-to-work-properly/706f2e89-05ff-4a4d-b74b-b74623df5c32?auth=1
that is from here on: HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\Current Config\WinLogon
Is there any way to do this securely as an domain user will have read access to the SYSVOL and the unencrypted .xml file which contains the username and password?
No… actually this is a very old post. So i would not reocmmend that you do it this way at all. Pretty much only do this as a very last resort and make sure the account has no special premissions.
Microsoft has an autlogon utility that allows the password to be encrypted instead of plain text. Sysinternals Autologon https://technet.microsoft.com/en-us/sysinternals/autologon
nice