Last week I showed you how to exclude an individual users from having a Group Policy Object (GPO) applied and this time I will show you how to properly apply a GPO to an individual user or computer. As I previously mentioned it is always best to use a security groups with GPO filtering even if you are only going applying it to a single user or computer. This avoids ever have to go back and modify the GPO security filtering if you need to add more object to the policy in the future.
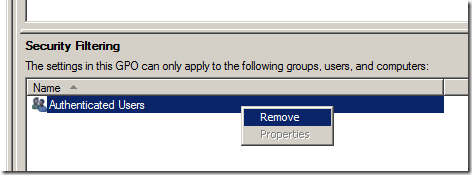
Note: Before I start I should point out a common mistake here is to remove “Authenticated Users†directory from the Security Filtering section on the Group Policy Object.
DONT DO THIS!!!
You should never do this as this however as this can cause “Inaccessible†(see image below) error messages on Group Policy Objects in the Group Policy Management Console for anyone who is not an Domain Administrator. This happens because you have removed the ability to for the user to read contents GPO but don’t worry this does not mean the policy will be applied to that user.
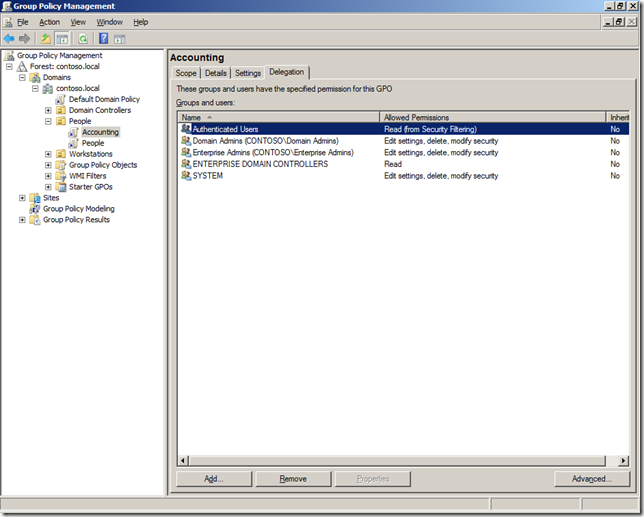
Step 1. Select the Group Policy Object in the Group Policy Management Console (GPMC) and the click on the “Delegation†tab and then click on the “Advanced†button.
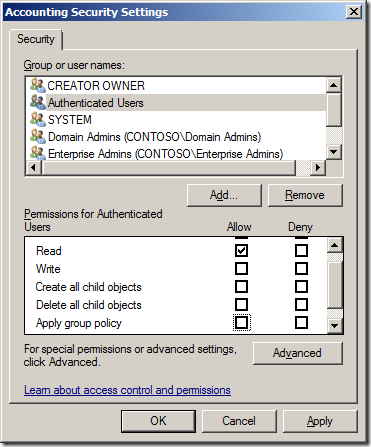
Step 2. Select the “Authenticated Users†security group and then scroll down to the “Apply Group Policy†permission and un-tick the “Allow†security setting.
Note: That the “Allow†permission for “Read†still needs to remain ticked as this prevents the Inaccessible message as mentioned above.
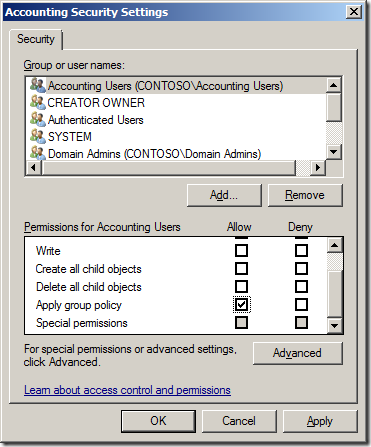
Step 3. Now click on the “Add†button and select the group (recommended) that you want to have this policy apply. Then select the group (e.g. “Accounting Usersâ€) and scroll the permission list down to the “Apply group policy†option and then tick the “Allow†permission.
This Group Policy will now only apply to users or computers that are a member of the Accounting Users security group. However you still need to remember that the user and/or computer still needs to located under the scope of the Group Policy Object for this policy to be applied.




How to apply a Group Policy Object to individual users or computer http://bit.ly/cDql7w
RT @alanburchill How to apply a Group Policy Object to individual users or computer http://bit.ly/cDql7w – Don't remove Authenticated Users
Best Practice: How to apply a Group Policy Object to individual users or computer: http://t.co/YLW2IPlT
Awesome!! best site ever in the subject.
Desktop Mangement & Consultant
YEAH. And now I could resolve a problem which appeared after two years.
Robert I agree, however as an IT Engineer of 26 years, mostly government, I would hope someone capable of creating such a detailed blog post with all the correct ideas, concepts, and graphics, would have someone proof read his material before publishing. I know it is nit picking, but it is extremely annoying to try and read a technical document with duplicate sentences one after the other, and so many grammatical errors. The frustration point almost makes one want to stop and look for a better readable document. However the author does eventually get the point across. But imagine being new to the English language, or new to AD and Windows Security to begin with, and getting lost in the grammar errors.
Just my two cents. Have a great day!!
@MarkjHurley Here's more info on your query on group poicy: http://t.co/5HWBw2p3 Hope this helps. ^Jess
Thanks a lot, you have solve me a big problem.
Thanks. Very clear and consise instructions.
I’ve done this with a specific computer (step 3), but the policy didn’t apply. Is this solution possible using a ‘User’ group policy and applying it to a specific computer?
why is it better to create another security group, and assign users to them and fiddle with delegation?
I am usually creating new OU (organization unit) and I will create a GPO on it. I will just add whoever I need to this OU.
Well, here is how I see it from my perspective, in an ideal world you are totally right about “I am usually creating new OU (organization unit) and I will create a GPO on it. I will just add whoever I need to this OU.”
But
there are times you want a policy to apply to many OUs and from experience this happens a lot AND user/computer can’t be in every OU but the security group can be.
Thank you Alan! Simplicity at its best…
Thank you for posting this article. In Step 3 of the instructions, can I add a computer, instead of a group name? I am asking this because I do not want to create an other OU just for one computer, and all the computers (except for two) in the desired OU already have the software (MSO2013). I know I could manually install the software on this two PC, but the same thing is going happen when new PCs are added to other OU, so it would be nice to be able to apply the gpo to install the software on the single PC in existing OU.
Thanks for your help.
Yes you could just add a computer…. but the point of using the group is that it makes it more discoverable if you look at the computer object group membership in AD.
Great article, but what’s the point of letting Non-Domain Admins read (and use) GPMC? This is counter-productive, you give “regular” users just the necessary permissions and tools they need to work, you don’t want those curious ones wondering around your Environment let alone spending time in GPMC when that’s not even part of their work.
If you need some Jr. Admin (Lets say HelpDesk) that doesn’t necessarily needs to be Domain Admin then just make a Sec. Group with those and Allow Read Permissions for those GPOs they might need.
Nevertheless they can always use ” gpresult /h c:\gpresult.htm ” to get detailed information of the enforced GPOs for machines and users.
Again, great article (good job) but don’t mislead readers and starter MS Shop Admins to non-Best Practices.
=] /Peace-Out\
The point is that many local admins on workstations are not domain admins but they can install GPMC. In fact many GPO administrators are also non-domain admins as some companies explicitly delegate permissions but removing the “authenticated users” from the GPO will leave it in a “Inaccessable” error message. The very nature of AD is that almost every thing is readable by the computers / users… Blocking the ability to see what is in the group policy only puts up road blocks for the GPO admins as they cannot see what policies might be applied to other users/computers.
What you are suggesting is to create a group that then grants “read” access to GPO after you have taken away read access…. That could work… but what would be the point? you are no more secure and now the setup is more complicated.
Great article and thanks for this sharing but it does not work for me. 🙁 May be I missed something but I have followed all the guide steps. Please advise.
Borin
Very nice & precise article Explain perfectly, Alan keep up posted.
It’s going to be ending of mine day, except before ending I am
reading this great post to increase my know-how.
Visit my web site acheter cialis 5 mg original
Great post. Thanks a lot for this.
I followed all your instructions, but only the user settings within the GPO will apply. I haven an additional question. Is it possible to apply one GPO to a user group and have both (user and computer) settings applied? Because a GPO always have a computer and a user part.
Thanks in advance
Lucky
Thanks for taking the time and effort to write this, as a blogger myself I know it take energy to produce these docs.
However just as Lucky and Brandon pointed out this does not work for computers ONLY for users.
I have tried the exact steps many times with a Group which has computers inside of it and non of the computers will receive the policy.
Hi Alan
We applied this in our network but all the users are getting the policy rather than what we set it to be targeting one security group.
Can you please advice what is missing? would patching and hotfixes not being applied be a good start?
Regards,
I have applied a GPO to enforce enableing screen savers and also setting it to be password protected. Set it up as shown in this article and gpresult /r shows it’s applied on the computer level but not on the user level. That said I don’t see the changes being applied. Way I’m setup (small home network):
1. Created a new OU under my domain in Group Policy Management
2. Dragged the GPO onto the newly created OU
3. Went into Active Directory Users and Computers
4. Moved the computer I want the screen saver applied to from “Computers” to the newly created OU
When the person logs in shows as above but no screen saver. Do I have to set something else up specifically for this policy to be applied to a specific user? I read something about enabling group policy loopback processing but not sure if that is relevant to a user. Thought that is when you want to apply a user based policy across the whole computer or something.
Thanks.
JR
great article, thanks for the walk-through!
Hi ,
I havev multiple OU’s every OU contains few users. We are migrated our exchange, Now what be want user from Any OU, Who have been migrated to new exchange can’t Import, Export or create PST. For That i have created a Group policy, Now i created one security group, Add that group into Group policy’s delegated assign read & apply group policy permission. Later add few users in that group from different different OU’s , User are still able to import & export the PST. note : same policy is working fine on OU but not on security group.
Please let me know which step i am missing.
Thanks for sharing this fantastic write-up !
Here is another informative article which summarizes the steps to enable Global Audit Policy in Windows server to enhance the security of organization : http://www.grouppolicyauditing.com/blog/enabling-global-audit-policy-in-windows-server-a-quick-security-guide/
Hi all,
Need your help…
I have GPO which applies to OU named VM and it has wsus test group which has all servers added into that now I want 4 servers out 100 should get this gpo
I created a group named wsus excluded and add them into the same
then I deny AGP permission under delegation tab
though servers are still getting gpo
I was wondering if this was because of authenticated user group which is by design there ??
Hi all,
Need your help…
I have GPO which applies to OU named VM and it has wsus test group which has all servers added into that now I want 4 servers out 100 should not get this gpo
I created a group named wsus excluded and add them into the same
then I deny AGP permission under delegation tab
though servers are still getting gpo
I was wondering if this was because of authenticated user group which is by design there ??
thx for article, it helped me to understand why my gpo is not working when i remove authenticated users.
Awesome. Thanks so much. My boss made that authenticated users mistake and thanks to this article I found the problem.
Thank you, everything was working fine till some time in the last month. This made it all work again. Glad I discovered it before my users noticed.
Thanks. I believe that will do what I need.
Thank you!! For a couple of years our network functioned fine despite the Authenticated Users mistake – and then suddenly it stopped working. I spent half a day trying to find out why – until this article explained what went wrong.
Hello
I created group policy to add specific site to local intranet zone for internet explorer
I run internet explorer as different user, but group policy is not applied it is only applied for the user logged on the system(Windows 7)
Is there any way to apply group policy for any users including run as different user
Thanks
Thankyou Thankyou and Thankyou – this has just eased the last 6 weeks of heartache…. The need to keep AuthenticatedUsers with ‘read’ permission was not something I had picked up anywhere else when applying GPO to User based/Security Groups
Hey,
thanks for this info, I tried exactly as you described, and it’s not working. The GPO still applies on the AuthenticatedUsers group.
And I found out why,
https://blogs.technet.microsoft.com/askpfeplat/2016/07/05/who-broke-my-user-gpos/
Hi Alan ,Hope you doing well.
i have one question i was applied Group Policy to Group but i want to apply in the group a different policy for example Screen lock on ideal time 2min which i did on this group.but i want in this group to have screen lock ideal time to 5 mins and other 2 minutes .How i do that and he also part of the same group.please Thanks
I want to apply 5 min Auto Screen lock policy to just one user and rest of the group have 2 min ideal time.
Hi, Anyone please reply to my question i am waiting for answer ?
The only thing I can think of is to create two GPOs. One for the single user and one for the group.
I am confused.
Why can’t you simply remove authenticated users from Security filtering and add the new group? Why would I get an error about authenticated users if the new group consist of users that log into the domain?Is this Microsoft making things that are easy, complicated again?
Hi
I have done as you have advised but am finding that when the authenticated users ‘Apply Group Policy’ option is un-ticked then the GPO doesn’t apply to anyone.
Just to give a run down, I have created a global security group in AD and added a list of server to it. I have then added this group into the security filtering of the GPO. I have removed the option for authenticated users to apply group policy but have left the read option ticked and on the group I added into the security filtering I have checked to make sure both apply the group policy and read are ticked.
When running GPRESULT from one of the group members it is showing that this GPO has been filtered out due to security.
Are you able to advise please?
many thanks
I’m getting the same issue.
Hi All,
Need a help.
I have observed that group policy is not properly getting applied to a Domain controller under “Domain Controllers” OU.
I need to exempt that faulty domain controller from a specific Windows time policy in a GPO, instead of exempting that DC from entire GPO as I need other settings to remain the same.
Can anyone help me in exempting the faulty DC from a specific policy in the GPO.
Thanks in advance,
Isha
can we implement Group policy on a specific user or no? if yes why n who? if no why ?
Argh, thanks! So in summary, Authenticated Users need to be able to read, but not apply the policy, then you apply the policy (with read permissions also) to the group you want it to apply to. 🙂
I deviated from your suggestion in the article, by adding the group to the scope option, which I like because now I can see who it applys to in the scope (Don’t know if your way does that too?).
Thanks so much. Very useful website!
I completely agree with Ed’s comment on 17/09/2016 at 4:19 pm. It’s extremely frustrating to have to weed through all the grammatical errors. Did you not proof this before publishing it? When I see so many mistakes (and I mean one after another) I immediately begin to doubt the technical soundness of the document as well. Come on people. Proof your documents before you present them to the public. I gave up on this and looked elsewhere for the answer.
For anyone on Server 2012 R2, removing the “Apply Group Policy” for “Authenticated Users” under the “Delegation” tab removes the “Authenticated Users” from the “Scope” tab. “Authenticated Users” still does have “Read” permissions in “Delegation” tab.
Can you help me for making a group policy application server
So this works great to install software to a group, thank you! My question is: is there a way to have it automatically uninstall the software if the computer is removed from the security group? It installs when I add them to the group but not when they are removed.
You need to enable the option in the applicaions deployment that the program is removed when it fall out of scope. This means that the computer is either removed from the group or to anohter OU that no longer applies that policy
Hey There. I found your blog using msn. This is a really well written article.
I will be sure to bookmark it and return to read more of
your useful information. Thanks for the post. I will
definitely return.
thank you 🙂
this was helpful, enable me to understand where I had difficulty.
thank you very much, this is very clear and helpful.
12 years on and this article is the only decent explanation. I must have read dozens of more recent ones that were utterly useless. Almost passed over this one at first glance due to the age.
Sometimes (I say all the time) you want to leave all your users in a single OU. But how to have GPO’s apply to only some individual users within that OU and not all of them?
This works exactly as Alan has shown, tested just now on Server 2019. Do not remove Authenticated Users, leave ‘Read’ ticked but remove ‘Apply Group Policy’ from it. Add your security group, and make sure both ‘Read’ and ‘Apply Group Policy’ are ticked. Also remember to link the GPO to the OU where the users are located.
Thanks, yes still amazing how people don’t know how to do this the right way…