One of the problem that face IT Administrators today is keeping up with all the security updates you need to deploy to your computers to keep them secure. This is even more exacerbated by the very large number of security updates associate with running multiple browsers. Also having multiple browsers on network could mean that you have totally patched one browser using your patch management system only to have user use a different type of browser that is completely un-patches. Another reason IT Administrators might want to block running third-party browsers is the lack of group policy support which makes it very difficult for administrators configured the browser to corporate standards (e.g. home page and/or security settings). Luckily Windows 7 comes with a new feature that prevent the user from running a particular executable called AppLocker which can be used to block all but authorised internet browsers.
Update: Also check out my Troubleshooting AppLocker workflow post at https://www.grouppolicy.biz/2013/04/how-to-troubleshoot-applocker/
AppLocker is a new feature in Windows 7 that allows system administrators to block a particular executable from running on a computer. This is a enhanced version of Software Restriction Policy which did a similar thing in Windows XP/Vista, but it can only block programs based on either a file name, path or file hash. The AppLocker feature takes it a step further and allows administrators block executables based on its digital signature. The benefit of basing this on a digital signature is that you can block programs based on a combination of the version, program name or even vendor name. This means that even if the vendor updates the program with a new version (which happens often with browsers) the AppLocker rules will still apply greatly saving administrative overhead. You can also set the rule based on the program version which means you can set a minimum supported versions that is allowed to run. Another advantage is that AppLocker applies to any program that runs on a computer meaning that no matter where the program is being run from (e.g. USB Memory stick) it will prevent it from running.
Note: You can also use this tutorial to block the running of any other program weather it be from a third-party or even from Microsoft. In this example I show you how to block running Google Chrome on any of your computers in your network however you can just as easily apply the same process to any other browser (e.g. Firefox, Safari).
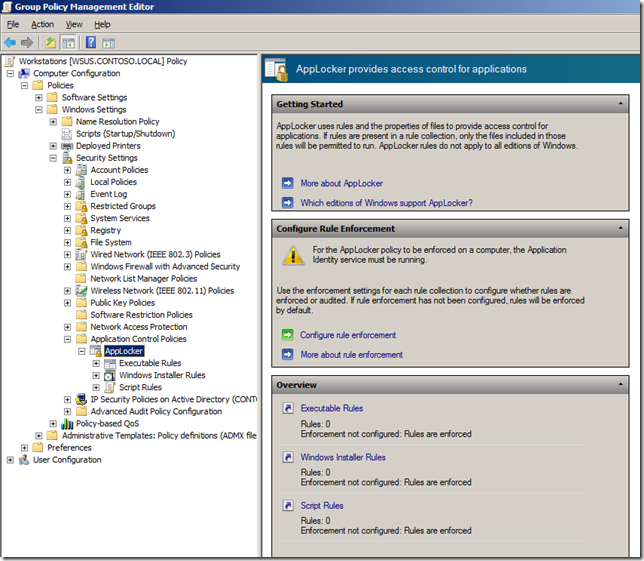
Step 1. Edit the Group Policy Object that is targeted to the computer you want to apply this policy. Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Application Control Policies and then click on “Configure rule enforcementâ€
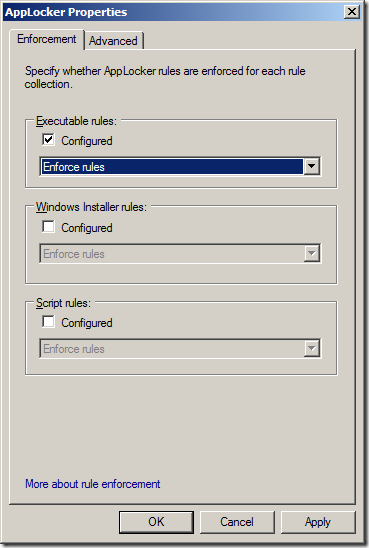
Step 2. Under Executable rules tick “Configured†and select the “Enforce rules†option from the pop-down menu then click “OKâ€.
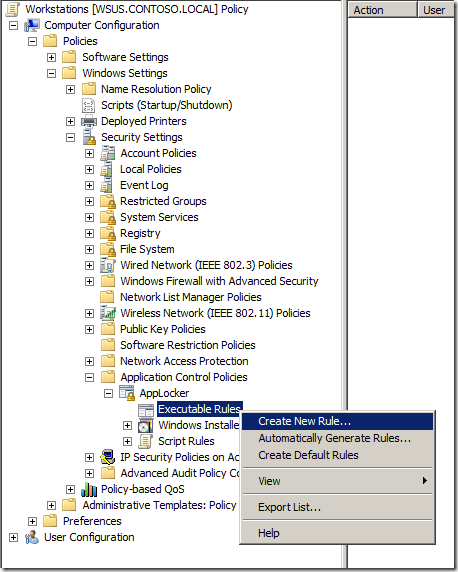
Step 3. Right click on “Executable Rules†and click on “Create New Rule..â€
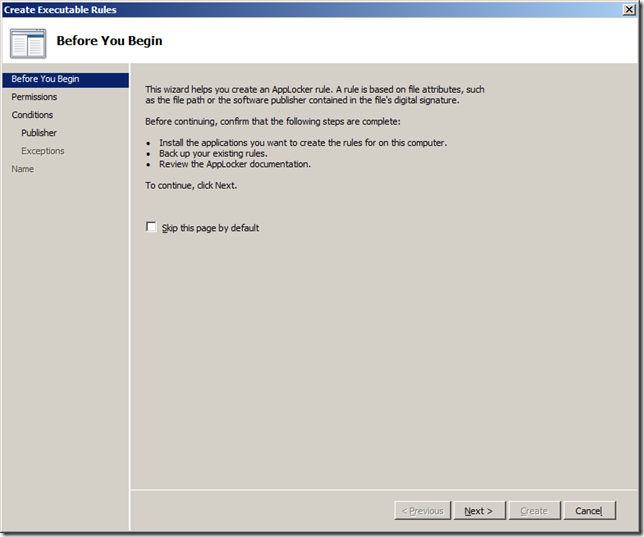
Step 4. Click “Nextâ€
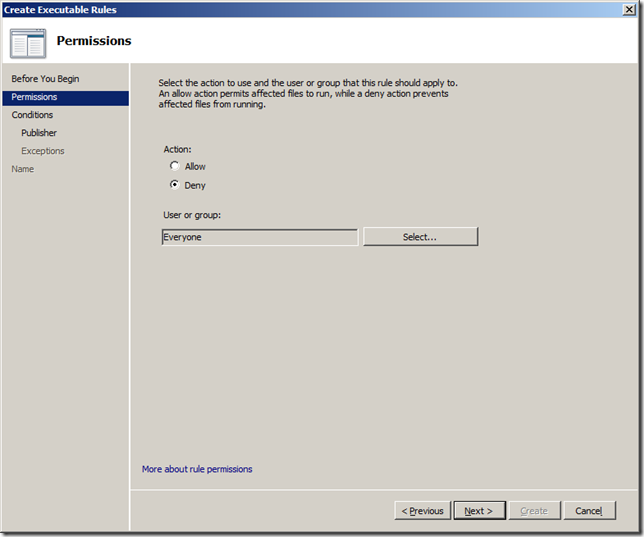
Step 5. Select “Deny†and then click “Nextâ€
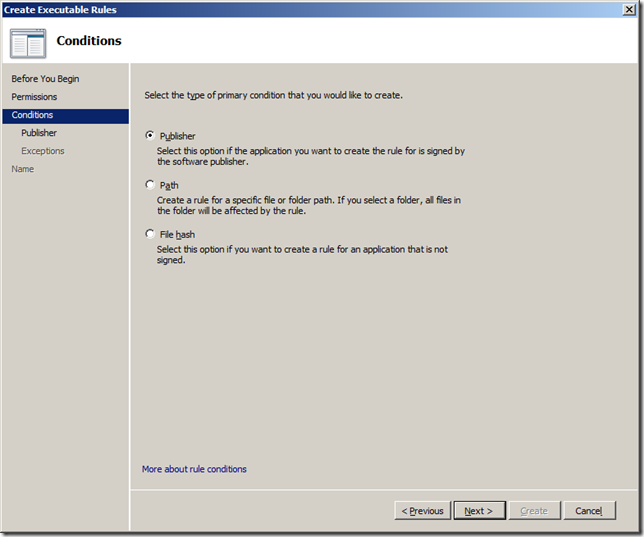
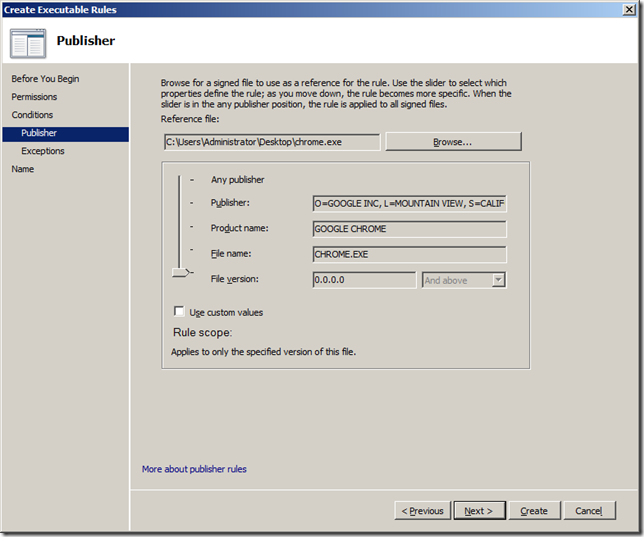
Step 6. Select “Publisher†condition and click “Nextâ€
Note: The “Path†and “File hash†option are the same condition as was available in a software restriction policy that was in Windows XP and Vista.
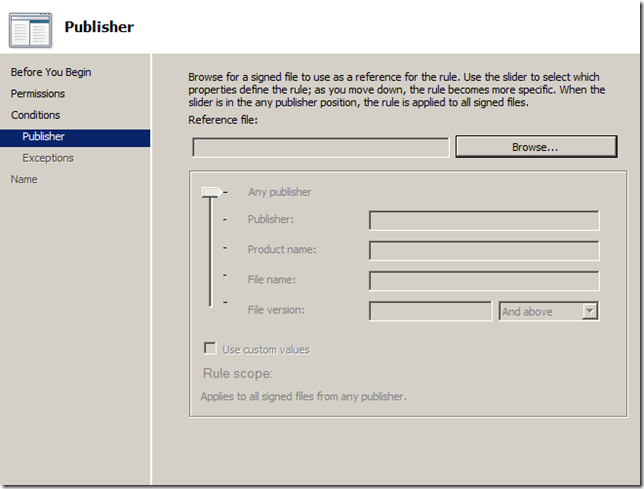
Step 7. Click on “Browseâ€
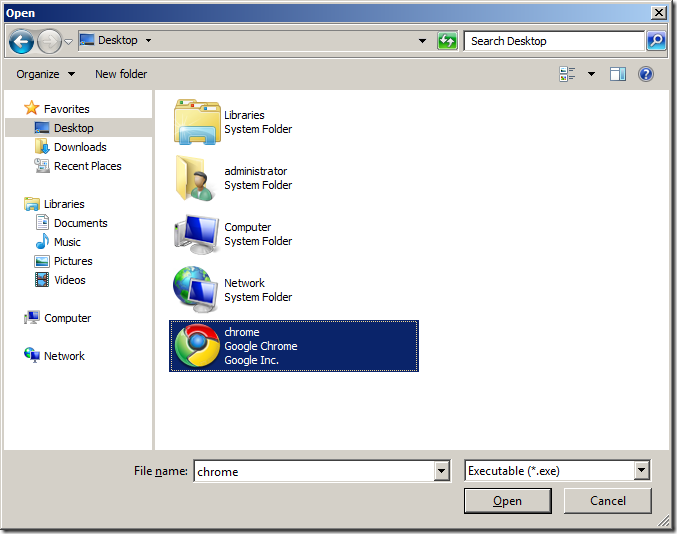
Step 8. Select the “chrome.exe†executable file and click “Openâ€
Note: Again I have used Chrome as an example you can easily select the executable of any other browsers (including Internet Explorer) here as well if you want to block multiple browsers.
Step 9. In this example we are just going to accept the defaults and click “Nextâ€.
Optional: If you wanted to just block a particular version of browser (or program) or just any version below a certain number tick “Use custom values†and then enter the version number in the “File version†field and select “And Below†from the pop-down menu.
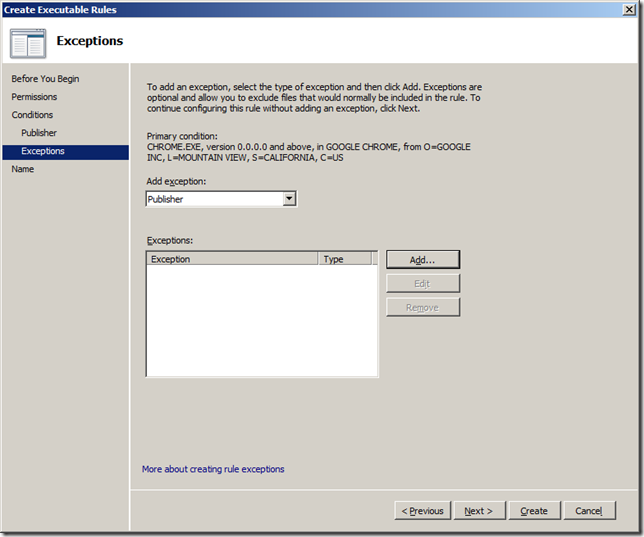
Step 10: Click “Nextâ€
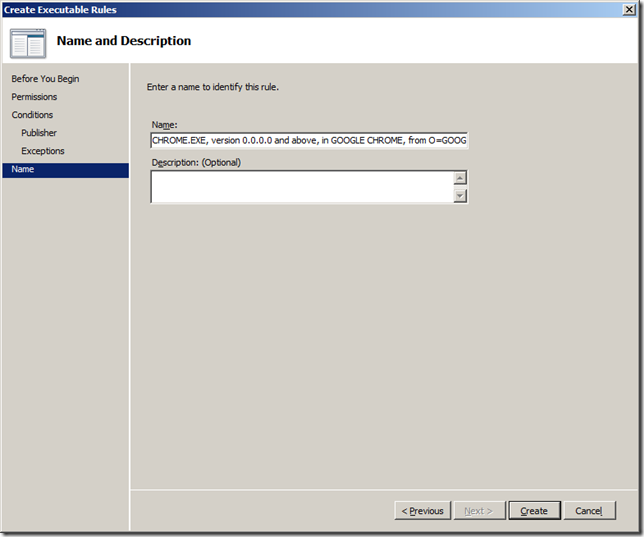
Step 11: Click “Createâ€
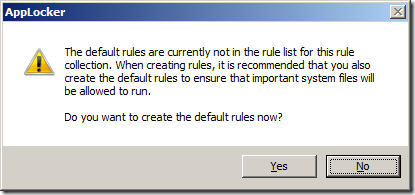
Step 12: You will now be prompted to create some default rules that ensure that you don’t accidently stop Windows from working. Click “Yes†to this if you don’t already have these rules created.
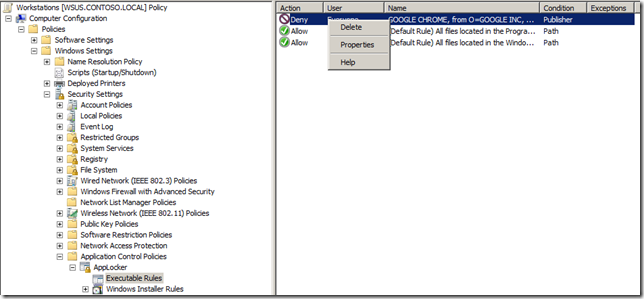
Step 13 (Optional): If you also want this AppLocker rule to apply computer administrators then right-click on the “BUILTIN\Administrators†rule and click “Deleteâ€
Step 14 (Optional): Click “Yesâ€
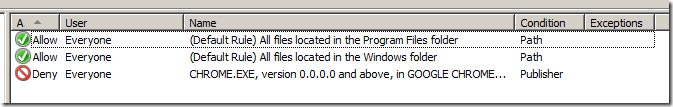
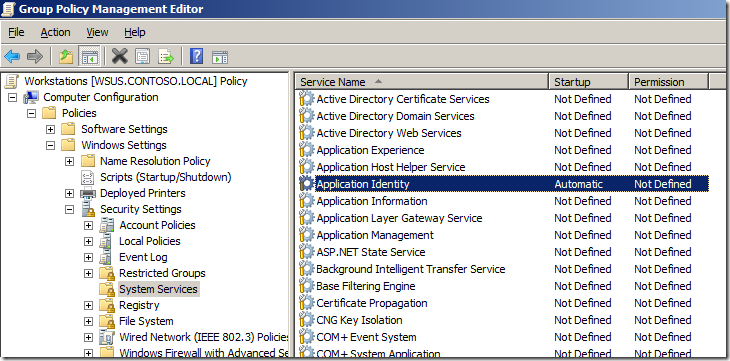
You AppLocker Rules are now setup and should now look like this…
Now there is one more thing you need to do to enable AppLocker on the computer…
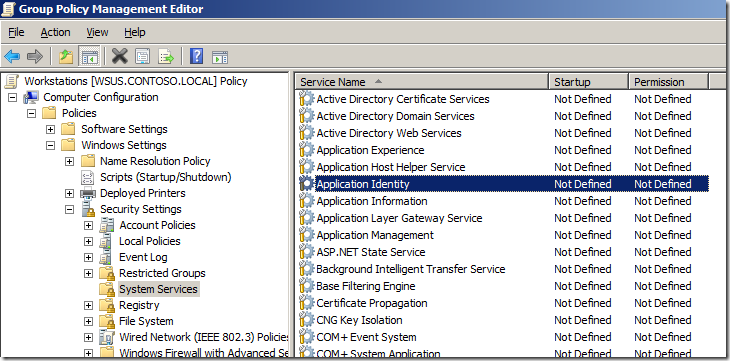
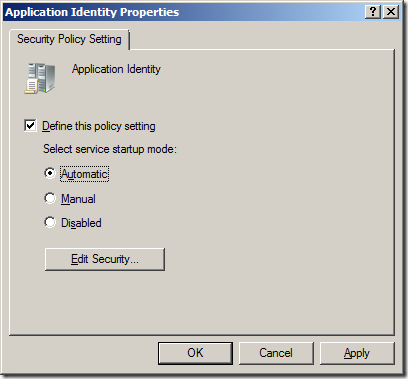
Step 15. In the same Group Policy Object you were just editing navigate to Computer Configuration > Policies > Windows Settings > Security Settings > System Services and double click on the “Application Identity†service.
Note: This is the process that scan’s all the file before they are executed to check the name, hash or signature of the executable before it is run. If this is not turned on then AppLocker will simple not work.
Step 16: Tick “Define this policy setting†and tick “Automatic†then click “OKâ€
The services section should now look like this…
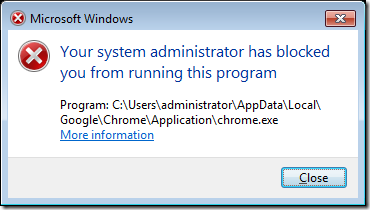
Your all done… Now when the user tries to run an un-approved browser (or program) they will be presented to this dialogue box…
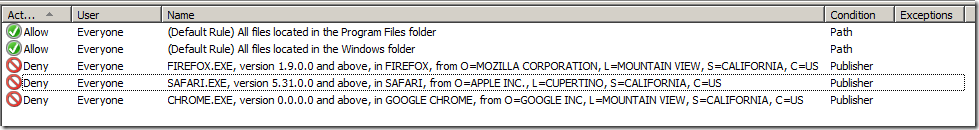
Now if you want to make sure you have covered all the bases below is a an image of the AppLocker rules configured with a few more denied browsers…




Blog Post: How to configure AppLocker Group Policy in Windows 7 to block third-party browsers http://bit.ly/98UPDh
How to configure AppLocker Group Policy in Windows 7 to block third-party browsers http://bit.ly/98UPDh
How to configure AppLocker Group Policy in Windows 7 to block third-party browsers http://is.gd/bsQ8s
Excellent tutorial! AppLocker is one of the unsung heroes of Windows 7, at least where IT administration is concerned. It should solve a lot of the hassles that arise from users running unauthorized apps.
if anybody want to endulge me i would be happy to block all types and all versions of torrent-clients. i guess it would be a long list so if somebody would like to maintain a webpage that i could update from it would be nice.
Yes… it would be a long list and Applocker will only work on application that have been signed digitally… and i would guese that most torrent clients are not digitally signed.
Thanks for sharing your helpful information
Whether – not weather.
Fruit bat or grammar nazi. Both are fun to watch squirm when proper stimuli are applied. Glad to see someone is on top of their game.
How can Applocker be applied with time segments i.e. different policies for different time brackets.
THANK YOU! The computer I’m going to enforce the rules is in Chinese and I can’t understand a thing. So it’s very helpful for you to include the screenshot for each the step. Thanks for the “extra mile” effort, really!
Thanks you the computer i m going on enforce the rules is in software Apploker systems is very good
This feature is great, but can i configure it to prevent another user on my computer (who by necessity has admin rights) from accessing applocker itself, to prevent them removing/editing the rules?
I know this response may be late, but I just came across this article while researching applocker. There is a way to lock down other local admins from modifying local or domain based group policy. It involves user rights assignment and file/folder permissions.
Example for local policies you want to protect:
Open the local group policy editor on the PC.
Drill down to Computer Configuration>Windows Settings>Security settings>Local Policies>User Rights Assignment.
Open the policy, Take ownership of files or other objects.
Remove the Administrators group from the list, then add only the good local admin user accounts that you want this policy to apply to. Click OK when done.
Locate gpedit.msc and secpol.msc, and regedit.exe. open their properties and access their security tabs.
add the offending local admin that you want to prevent from running these apps, to the ACL and Deny full permissions.
Set the same permissions for the offending local admin again for the following folders: C:\Windows\System32\GroupPolicyUsers and C:\Windows\System32\GroupPolicy, to prevent them from deleting the local policies.
A policy like this can also be similarly made in domain based GPO as well.
These steps should block the specific offending local admin(s) from opening these editors. They will also be unable take ownership of files and folders to be able to give themselves full permissions to them again in order to change policies.
Have fun!
Ryan
I still would not consider that a 100% solution as a local admin could still disable the group policy and undo all the restrictions you apply to the computer. The best thing to do would be to remove all local admins… not try to restrict them.
But Kudos for creative thinking…
i did like this but but didn’t work
here what i did
create new gpo and link to my computer ou
Thank you for this interesting article. I published an article about AppLocker even on my blog at http://www.dertechblog.de/?p=3795. Your article really helped it. Thank you Alan.
This policy works when a user trying to install a chrome browser. Incase the users already installed the chrome ,Is this policy stops the browsing on already instilled browser?
Yes, that’s what it does.
Step 13 and 14 claim to be optional if you want to block Administrators also, but since Deny rules override Allow rules, the Administrators will be blocked anyway even you skip 13 and 14, correct?
What stopping the user downloading and renaming the .exe for example chrome.exe tblog.exe
Chrome.exe is a signed file, so Applocker checks the publisher, product name, version in the signature. This signature remains even if the file is renamed.
Take freeware http://www.processblocker.com and configure it as:
Blacklist:
*
Whitelist:
%programfiles%\*.*
%programfiles(x86)%\*.*
%windir%\*.*
Now users cannot run/install anything else that administrator intalled for them, even if user renames the file or trying to run it from Desktop or USB flash drive
So where are the best practices?
This is a multiple page article… did you following the link at the bottom of the pages to the other articles?
FYI… I have not made this a single page post again…
in the windows help for app locker, it said that app locker rules cannot be enforced on computers running windows 7 professional. if this this true, that’s mean it is useless to me because all of my company computers are using 7 professional
yes that is correct… I also have this in my troubleshooting guide as this is a common cause of AppLocker not working. https://www.grouppolicy.biz/2013/04/how-to-troubleshoot-applocker/
I am currently trying to set up rules in AppLocker using hash values. Every time I try to create a new rule for an executable file I get an error message saying “Value does not fall within the expected range.” I am however still able to create rules based on publisher and path as well as a hash rule for a .msi file. How can I prevent this error from occuring and create rules based on hash values for executables?
Thank you for your time. Still a good step by step guidance. Though I am late but the technology still in good stand.
hey there and thank you for your info – I’ve certainly picked up anything new from right
here. I did however expertise some technical issues using this
site, since I experienced to reload the site lots of times previous to I could
get it to load properly. I had been wondering if
your web host is OK? Not that I am complaining, but slow loading instances
times will very frequently affect your placement in google and could damage your quality score if ads and marketing with Adwords.
Well I am adding this RSS to my e-mail and could look out for a lot more of your respective interesting content.
Make sure you update this again soon.
Excelente articulo.
Saludos desde Venzuela
Would it be possible to do all this via command line/cmd ??
Hello,
Right now, I’m trying to implement Applocker in my company, recently I’ve tried it, but there is a big question is my head about the default rule. There are 3 defaults rule:
– For the windows folder
– For the Program File folder
– Built-in Administrator
I used a reference computer to use its policies, I exported then imported it to the GPO. In the policies, there are 3 default rules, and another rules generated using “Automatic generate rule” from the program file folder.
I imported the policies to the GPO, I implement the applocker for executable file at some clients.
The big question is: what if the user install new app/software to their computer? It should be blocked right, because the policies from “Automatically generate rule” doesn’t allow that, but the default rules said that all file at the program files are allowed, which all app/software installed will go to the program file folder. I tried to install new app on my computer, but I can run it. So there are like two policies that override each other. What do you think?
HI Experts
i need to block any executable files installation for ordinary users .so how can i get this .
as i have seen that some users that joined to domain and are not local admin but still they can run exe files .
in Applocker we need to define specific softwares but i need to block all installation for ordinary users .
thanks in Advance . your reply will be Highly Appreciated !
good work. I like your article. http://www.amirpc.com/wavepad-sound-editor-7-09-crack/
Hello,
I am trying to use AppLocker for users that are logging into a Windows Server 2012R2 and using Remote Desktop Services. From what I read and understand, the AppLocker will work for those logins as well. However I cannot get it to work. I have the default executable rules setup and a deny rule for one app that we do not want people to run.
Any advice?
I can send screen shots or anything else you may need.